Found in Environments Protected By:
Cisco IronPort, Microsoft
By Emmett Smith, Cofense Phishing Defense Center
Government grants provide unique opportunities for businesses to provide the means to invest if needed. Recently, analysts at the Cofense Phishing Defense Center (PDC) have observed a phishing campaign attempting to impersonate the US Small Business Administration (SBA), offering these SBA grant scams in the hopes someone unfortunate will provide their credentials.
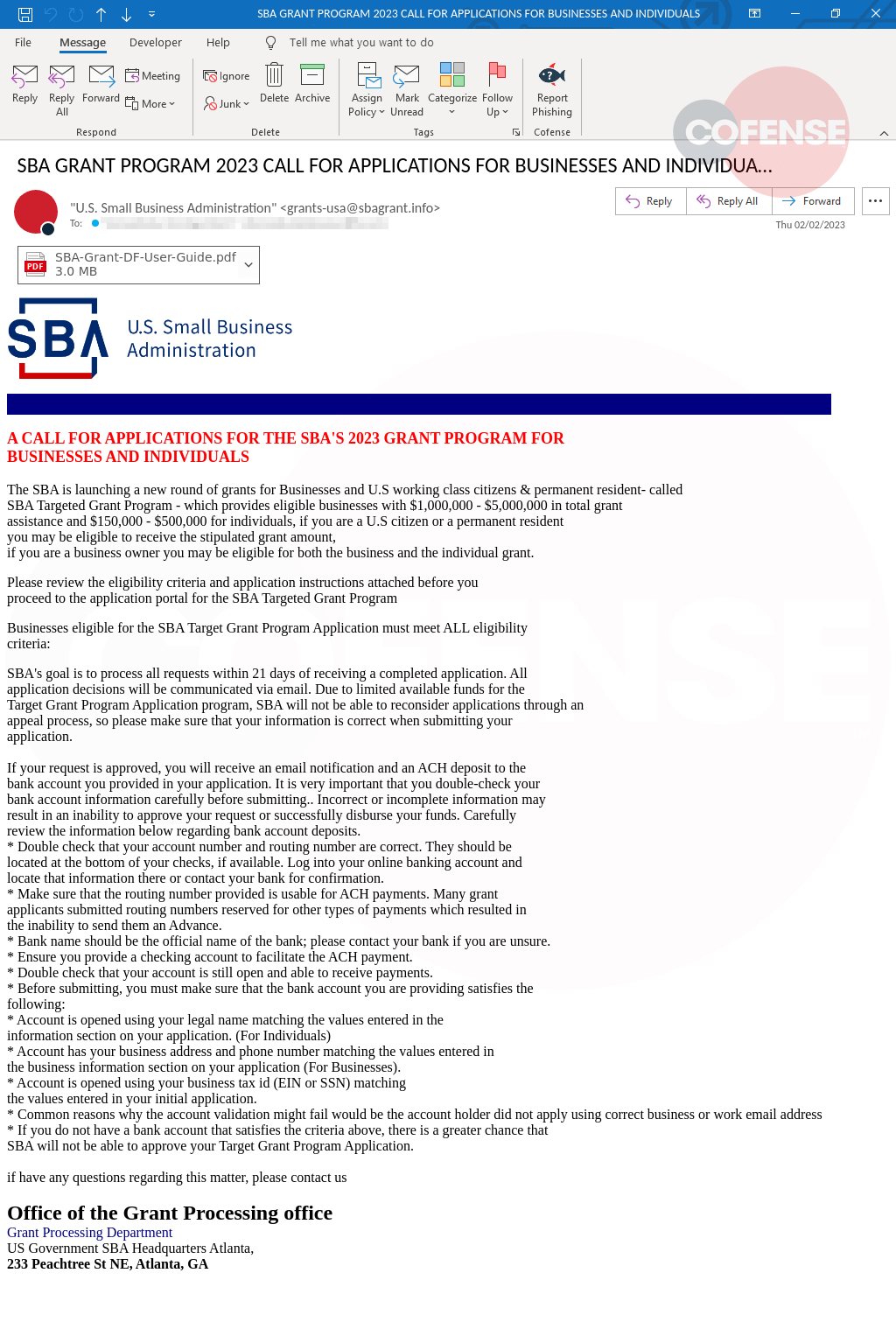
Figure 1: SBA Grant Scam Email
Figure 1 shows that the email body is quite lengthy and contains branding reminiscent of the SBA. The threat actor spoofed a seemingly legitimate email address, [email protected], which might be good enough to trick the recipient if they do not pay enough attention.
Looking closer at the body of the email, the threat actor most likely scraped this email from a legitimate inbox and repurposed it for their campaign. The email contains the legitimate address for a district office in George. With this, there is also a list of things the user will have to check for and information they will need to provide if they are to apply for the illegitimate grant. Attached to the email is a PDF file containing a link to the phishing site.
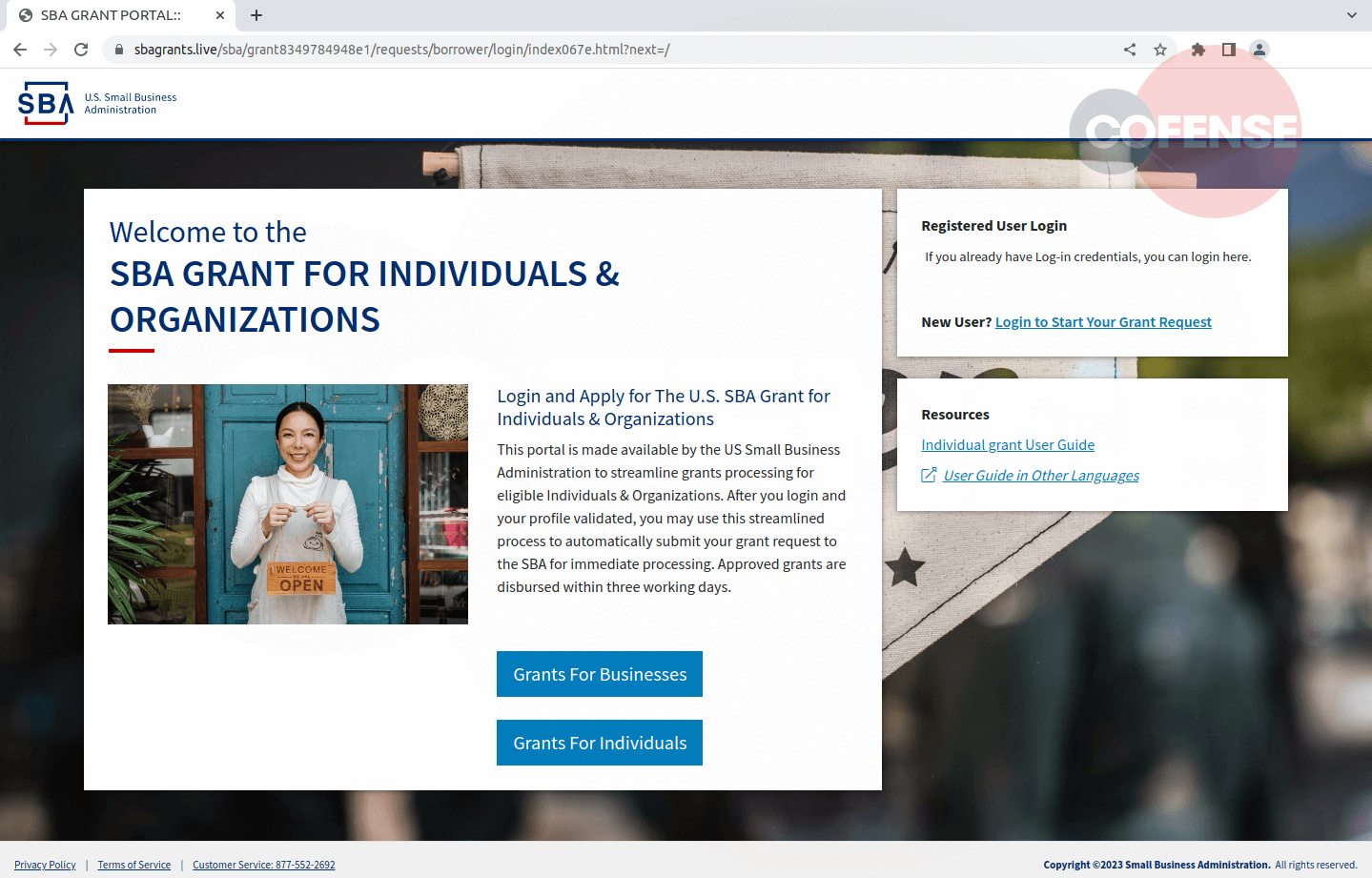
Figure 2: SBA Grant Scams Phishing Page
Figure 2 shows a legitimate-looking page for SBA, most likely spoofed from the legitimate SBA loan page. The URL address shares the same trait as the email address from earlier in that it is designed well enough that if the user does not pay enough attention, they may not notice it is an illegitimate URL. The text on the page itself offers a little bit of information on the purpose of the page, and at the top right corner, there is a link to log in.
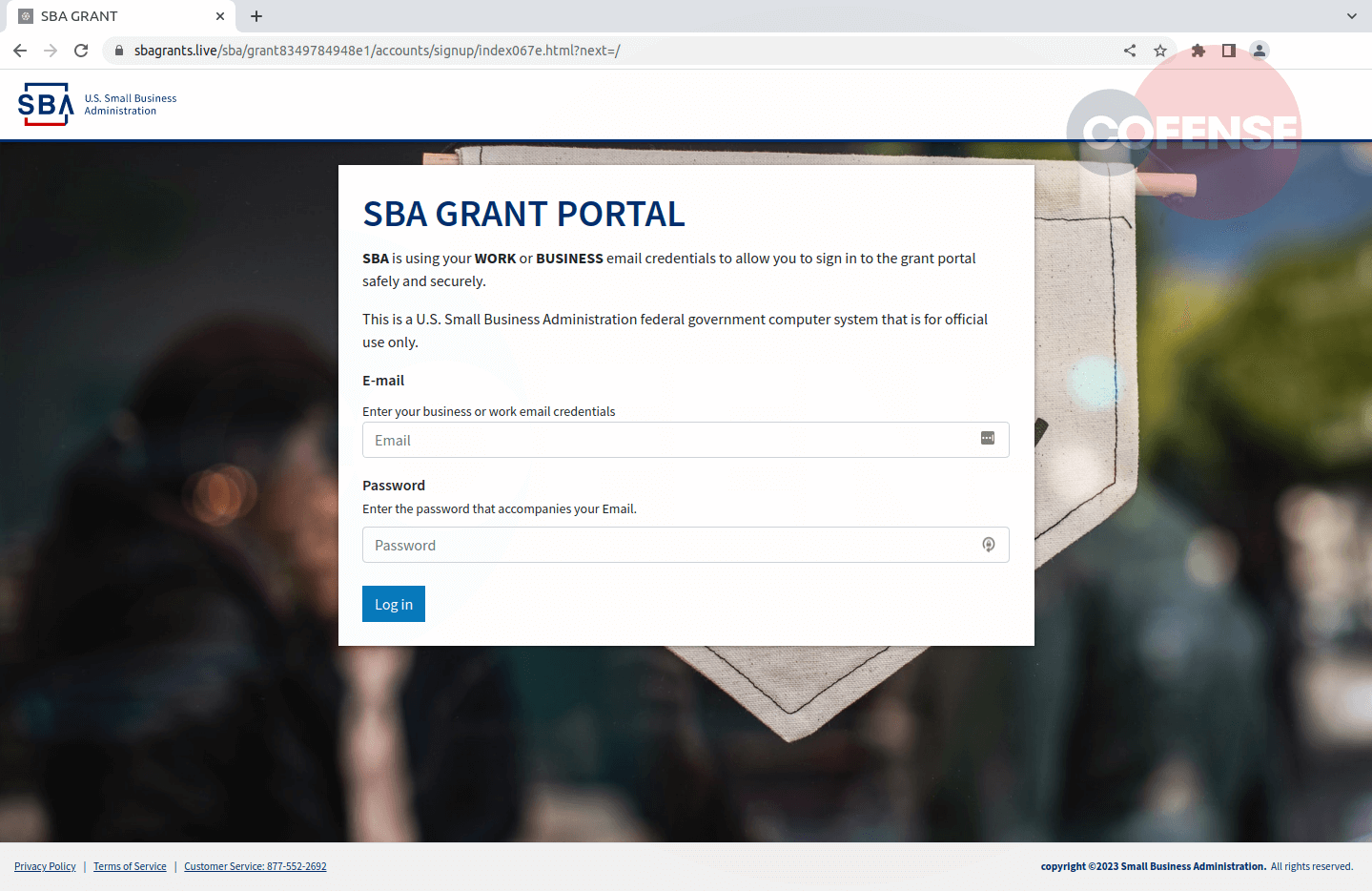
Figure 3: SBA Grant Scams Phishing Page
The login button from the previous page leads to the one in Figure 3. Comparing the two URLs the domain did not change. The threat actor even kept the same blurry background, branding, and information at the bottom of the page. They included many of the formatting elements from the legitimate site to raise the confidence of the recipient applying for the fake grant.
A grant can be a very tempting proposal for an individual or a business. Any plan offering money would pique anyone’s interest. With the strategy and design techniques the threat actor deployed, this campaign can be even more dangerous. Despite these tricks, analysts at the Cofense Phishing Defense Center (PDC) were able to catch this phish and provide protection.
If you would like to learn more about how the PDC can save you, contact us.
| Indicators of Compromise | IP |
|---|---|
| hxxps://sbagrant[.]info/grant | 95.217.36.56 |
| hxxps://sbagrants[.]live/sba/grant8349784948e1/requests/borrower/login/index067e.html | 66.206.4.66 |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.