Microsoft 365 ATP
Recently, the CofenseTM Phishing Defense CenterTM observed a phishing attack against American Express customers, both merchant and corporate card holders. Seeking to harvest account credentials, the phishing emails use a relatively new exploit to bypass conventional email gateway URL filtering services.
Email Body
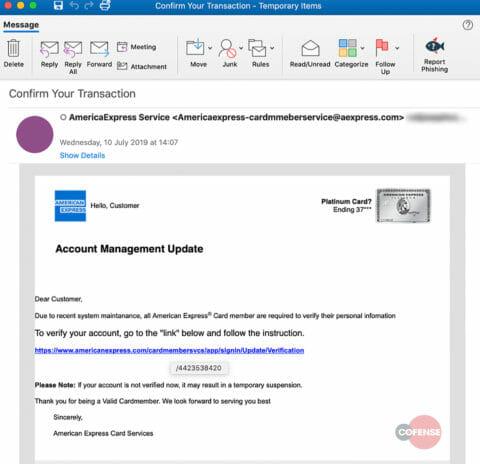
Take a look at the email below—the body of the message is riddled with grammatical errors. It asks the would-be victim to verify his or her personal information “Due to a recent system maintenance” and says that failure to comply would lead to a “temporary suspension” of the account. This is a tactic we see from attackers all the time. Threats of suspension to critical business systems and assets create a sense of urgency and panic. After all, people do silly things when under stress.
Figure 1, Phishing Email
The victim is urged to click on the hyperlink: hxxps://www.americanexpress[.]com/cardmembersvcs/app/signin/Update/Verification
At first glance, this looks like it could be a legitimate site, but instead contains an embedded “base href” URL which leads to the phishing page.
Message body in HTML
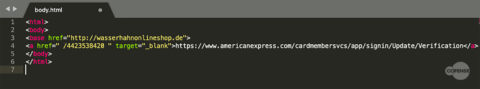
If you take a closer look at the hyperlink, you can see that the attacker is using a base HTML tag to split up the malicious URL into two pieces. The <base href=”hxxp://wasserhahnonlineshop[.]de”> tag contains the top level domain of the phishing page. HTML uses this domain as a “base” or building block for any URL when a href tag is called further down the page.
In the HTML snippet below, “/4423538420” is specified as the href for the embedded hyperlink. These two elements are combined to create the malicious phishing URL: hxxp://wasserhahnonlineshop[.]de/4423538420. This tactic helps the attacker evade URL filters and gateways that have active URL scanning services, which currently do not have the capability to combine these inert pieces into a scannable malicious URL.
Fig 2. Email Body in Plain Text
Phishing Page
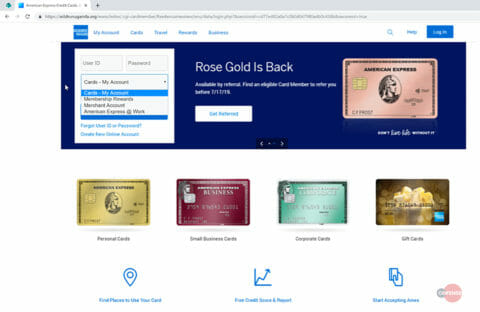
The main phishing page is a simple imitation of the American Express login portal. The attacker is clearly after four separate types of accounts via a drop-down menu the victim can select. These accounts include:
- Cards – My account (a personally held American Express account)
- Membership Rewards accounts
- Merchant Accounts
- American Express @ Work (corporate accounts)
Gateway Evasion
This email was found in an environment using Microsoft’s Office 365 Advanced Threat Protection (ATP).
Conclusion
This is a good example of attackers blurring the lines between consumers and business users, targeting a wide range of bank account types. The broad stroke attack would be very efficient when sent en masse, especially with its clever technique for bypassing URL filters and email gateways.
How Cofense Can Help
75% of threats reported to the CofenseTM Phishing Defense CenterTM are credential phish. Protect the keys to your kingdom—condition end users to be resilient to credential harvesting attacks with Cofense PhishMeTM. Cofense is the only company that combines a global network of 30 million people reporting phish with advanced AI-based automation to stop phishing attacks fast. Learn more about our holistic phishing detection and response solution here.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks.