By Harsh Patel and Zachary Bailey, Cofense Phishing Defense Center
Dealing with a ransomware attack on any businesses, organizations – or individuals – can turn into a nightmare scenario quickly. Ransomware typically has a two-pronged attack style. It not only denies the target access to their own computer, but it also attacks targets monetarily by demanding some form of payment to relinquish control.
This type of malware attack can be carried out through various methods with one of the most popular being through phishing emails. Over the past year with the rise in ransomware attacks, Cofense has observed threat actors delivering reconnaissance and data exfiltrating tools ahead of the final ransom attack. In early November, the Cofense Phishing Defense Center (PDC) intercepted and analyzed such an email that made its way into the inbox of targets using a secure email gateway (SEG), and it delivered a Halloween-themed MIRCOP ransomware.
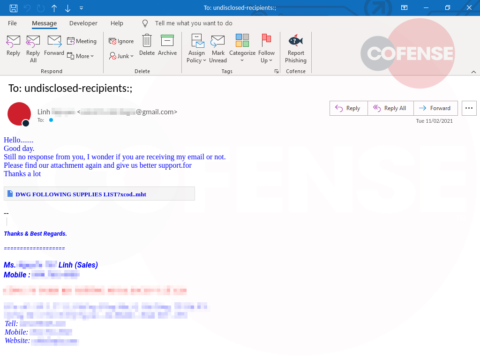
Figure 1: Email Body
Figure 1 shows that the email contains a lot of suspicious indicators such as a generic “from” domain and a subject saying “undisclosed-recipients.” In the email body itself, the threat actor is trying to suggest communication was lost for a previous arrangement and wanted support for a “DWG following Supplies List” that is hyperlinked to a Google Drive URL. Once clicked, the infection URL downloads an MHT file.
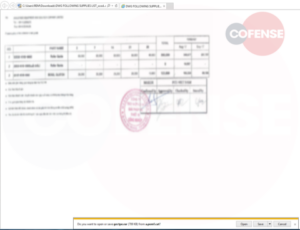
Figure 2: MHT File
MHT file extensions are commonly used by web browsers as a webpage archive. Figure 2 shows that after opening the file the target is presented with a blurred out and apparently stamped form, but the threat actor is using the MHT file to reach out to the malware payload (hXXps://a[.]pomf[.]cat/gectpe.rar).
Figure 3: RAR File
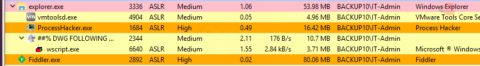
Figure 4: EXE File
As shown in Figure 3, the downloaded RAR file contains an EXE file. The executable is a DotNETLoader that uses VBS scripts to drop and run the MIRCOP ransomware in memory.
Figure 5: MIRCOP Ransomware Activated
After a few minutes, the ransomware starts the process of taking a screenshot, locking files, changing the background and running a program to find stored passwords in web browsers. MIRCOP ransomware is fully activated when the screen flashes, and the home screen is changed into the ransom note featured in Figure 5. The image dropped is extremely gory and will most likely deliver a shock to the user when coupled with the ransom message. The use of Skype as a medium to negotiate is uncommon, as most organized ransomware gangs have dedicated sites or mobile chat apps.
The MIRCOP ransomware, also known as Crypt888 ransomware, encrypts users’ files to hold them hostage. After the payment demand is met, the threat actor promises to provide the decryption method. For this attack, the threat actor gives a set of instructions on the wallpaper. The user is also unable to open any applications besides a few web browsers that can give them access to their email address which is used to contact the attacker. The email address is then used to set up the payment required to gain access to the decrypting tool the threat actor claims will unlock the files and applications.
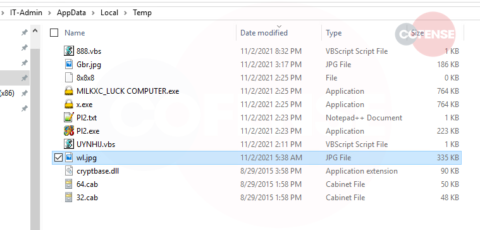
Figure 6: Files Saved in Temp Folder
The file named Pl2.exe was originally named “Web Browser Pass View,” which is a tool known for retrieving passwords from the vaults of common web browsers. The executable’s icon shows Internet Explorer, Google Chrome, Firefox, and Opera, referencing its targets. Looking up the SHA256 hash of this executable on Virus Total, it can be linked to dozens of malicious executables going back to June of this year.
The files stored in the Temp folder associated with the malware:
- Gbr.jpg – The screenshot that was taken after running the malware
- 888.vbs – VBS scripts to automatically detonate the ransomware
- MILKXC_LUCK COMPUTER.exe & x.exe – used to lock the files
- Pl2.exe – The password utility known as “Web Browser Pass View”
- PI2.txt – Where the passwords get stored
- UYNHIJ.vbs – The VBS script that’s run by the DotNETLoader
- Wl.jpg – Original image that replaces the current background
The MIRCOP ransomware poses a threat to medium-sized organizations as it can lock the files on critical computer systems. Its opening lure is business-themed, making use of a service – such as Google Drive – that enterprises employ for delivering files. The rapid deployment from the MHT payload to final encryption shows that this group is not concerned with being sneaky. Since the delivery of this ransomware is so simple, it is especially worrying that this email found its way into the inbox of an environment using a SEG.
In this case, a well-conditioned user quickly reported this email. They used Cofense Reporter, allowing the PDC to quickly identify the threat, allowing the organization to mitigate a potential incident. With Cofense Managed Phishing Detection and Response, provided by the PDC, enterprises can have our complete view of threats. Contact us to learn more.
Indicators of Compromise:
File Name: DWG FOLLOWING SUPPLIES LIST_xcod..mht MD5: 9fee0de10d34f9e4fd53d5ef5e606b39 SHA256: 2eaa031bae075d1c703c706383bef403ddcb94d332bfe6c1622a76f2d4c9f572 File Size: 707213 bytes | |
| File Name: gectpe.rar MD5: c32d544fe375c3ecf031bdf53f479e26 SHA256: fe42dc8d01dba7f857a3d9468856e3e177fc87111b2d779e1daeb5f5f4f43546 File Size: 808853 bytes | |
| File Name: ##% DWG FOLLOWING SUPPLIES LIST.exe MD5: 4b5742ff803d73c6a6b8301e4031ac4a SHA256: afd06217edd6cb3d1cbb7510ad26987ba3f7587d5f9d679ba06c587758622e9a File Size: 1182021 bytes | |
| File Name: Pl2.exe MD5: 8104093918B6F2D2004535B24B1533BA SHA256: 337A646E6F1A641D9471B840EE21BFF858E6BA24538A4F815191BE85E5003E70 File Size: 227840 bytes | |
| File Name: BTVTLU_LUCK COMPUTER.exe MD5: 6BFBD5CEC2A29ED6FB0780D0007F84B9 SHA256: F5D7586ECDECAF6E85C0B5865D1BD8280824B5D41A7A93833F8FB7BEFD50FDBE File Size: 781722 bytes | |
| File Name: 888.vbs MD5: 8BE57121A3ECAE9C90CCE4ADF00F2454 SHA256: 35D7204F9582B63B47942A4DF9A55B8825B6D0AF295B641F6257C39F7DDA5F5E File Size: 280 bytes | |
| Infection URL | hXXps://drive[.]google[.]com/file/d/1gm_jkT6Fga7F9m_0dzPcWBg3bXZMiiQC/view?usp=drive_web |
| Payload URL | hXXps://a[.]pomf[.]cat/gectpe.rar |