By Brad Haas, Cofense Phishing Defense Center (PDC)
In 2022, over two-thirds of campaigns reported to the Cofense Phishing Defense Center (PDC) involved URLs with subdomains. In about 5% of campaigns, threat actors chose subdomains tailored specifically to the targeted organization or user. Tailored subdomains may be more convincing than generic phishing URLs, but fortunately they are also likely to be more detectable. In this report we explore credential phishing threat actors’ use of subdomains in general and tailored subdomains in particular, as well as methods network defenders can use to counteract them.
How Threat Actors Use Subdomains
A subdomain is a prefix added to a domain name as a simple way to distinguish between different hosts or sections of the network within an organization. For example, Cofense’s domain name is cofense.com, and uses a subdomain for its Customer Resource Center: support.cofense.com. Subdomains are common in the email landscape as well, including many legitimate services delivering benign emails. Common examples include email marketing systems, business productivity suites, and website design tools.
Although nothing about subdomains is inherently malicious, threat actors can abuse them to make phishing URLs look more legitimate. Creating subdomains requires a certain amount of privilege within a domain, which threat actors can gain in a variety of scenarios:
- Dedicated malicious domains: Threat actors may use their own domain that they registered entirely for phishing purposes, in which case they have full control over subdomains.
- Hijacked websites: If threat actors gain administrative access to a legitimate domain, they can create subdomains for it.
- Website builders or collaboration tools: Services that allow users to design websites or collaborate on documents often create a subdomain for each project, and some of them allow the user to choose the subdomain. Threat actors abuse this capability by choosing deceptive subdomains.
Subdomains Are Common in Credential Phishing Campaigns
We investigated subdomain usage in all the credential phishing URLs reported to the Cofense Phishing Defense Center (PDC) in 2022, a data set reflecting real-world campaigns that reached user inboxes at organizations using a variety of secure email gateways (SEGs). We found that malicious emails used subdomains frequently: 69% of reported emails throughout the year involved a URL with a subdomain. Many of those campaigns abused legitimate services that use subdomains in their URLs, which raises the overall total. However, even when we removed duplicate domains from our analysis, the number of URLs that involved subdomains was still 34%.
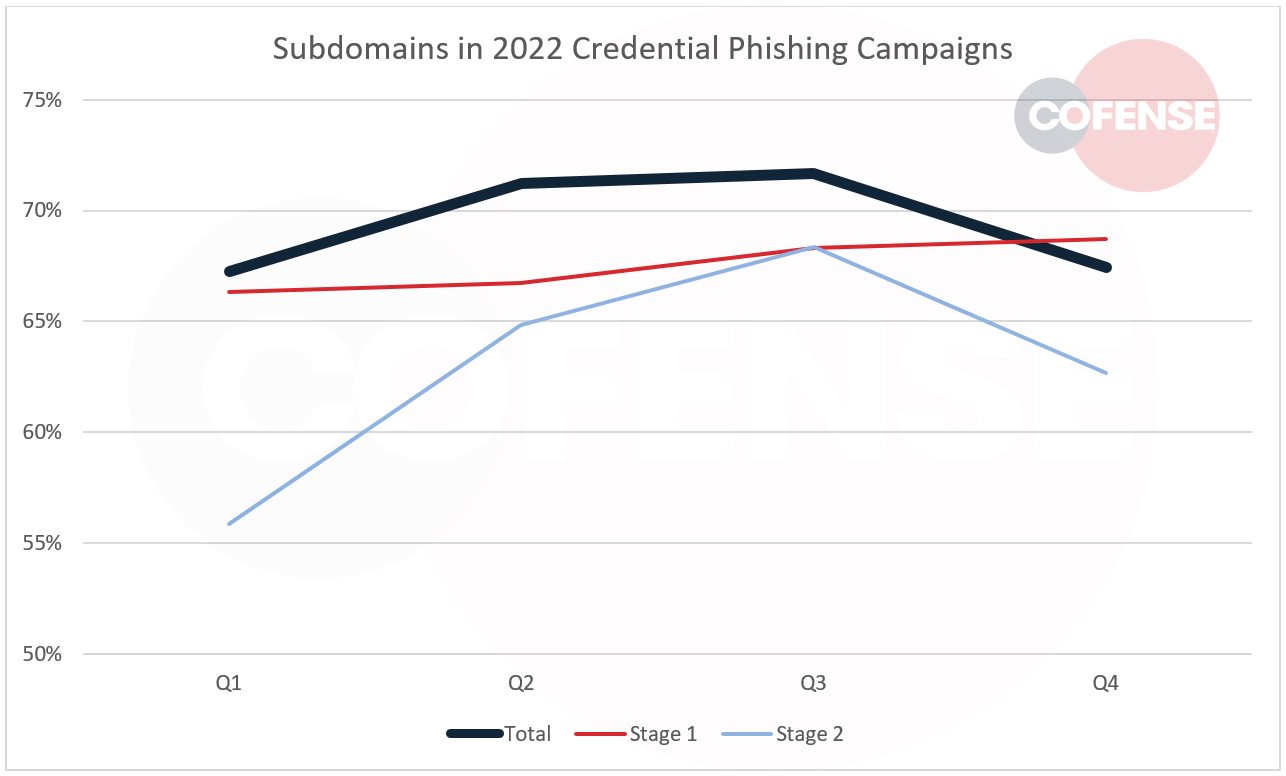
Figure 1 shows a breakdown of subdomain usage by quarter in 2022. The graph includes totals divided between the two stages of credential phishing attacks. Stage 1 represents URLs embedded into emails or email attachments. Stage 1 URLs have to pass inspection by SEGs to reach inboxes, and users have to click on them to open them in a browser. Stage 2 includes any URLs later in the attack chain, such asadditional redirects or exfiltration URLs.
Figure 1: Percentage of credential phishing campaigns that included subdomains in 2022.
Figure 1 shows that subdomains are more common in stage 1 URLs. The value of subdomains for threat actors probably diminishes in stage 2, when a user has already accepted a link as legitimate and it is no longer subject to inspection by SEGs.
The exact subdomain that a threat actor chooses for a campaign depends generally falls into one of three categories:
- General deceptive subdomains include terms that a user might expect to see in a URL, drawing their attention away from a suspicious primary domain name, e.g. login-security.example.com.
- Randomized subdomains (for example asdfadsfghasdg.example.com) simply obfuscate the malicious URL, which may make it more likely to avoid blocklist-based detection.
- Tailored subdomains involve something specific to the user or their organization. The most common version in our data is the primary domain of the organization (which is often its name), e.g. cofense.example.com.
Tailored Subdomains Provide Customized but Detectable Attacks
Tailored subdomains offer threat actors multiple benefits at once. Using a different subdomain for each targeted organization or user helps malicious emails evade blocking that is executed based on entire URLs or entire subdomain.domain combinations. At the same time, the customization gives the malicious URL some appearance of legitimacy to targeted users.
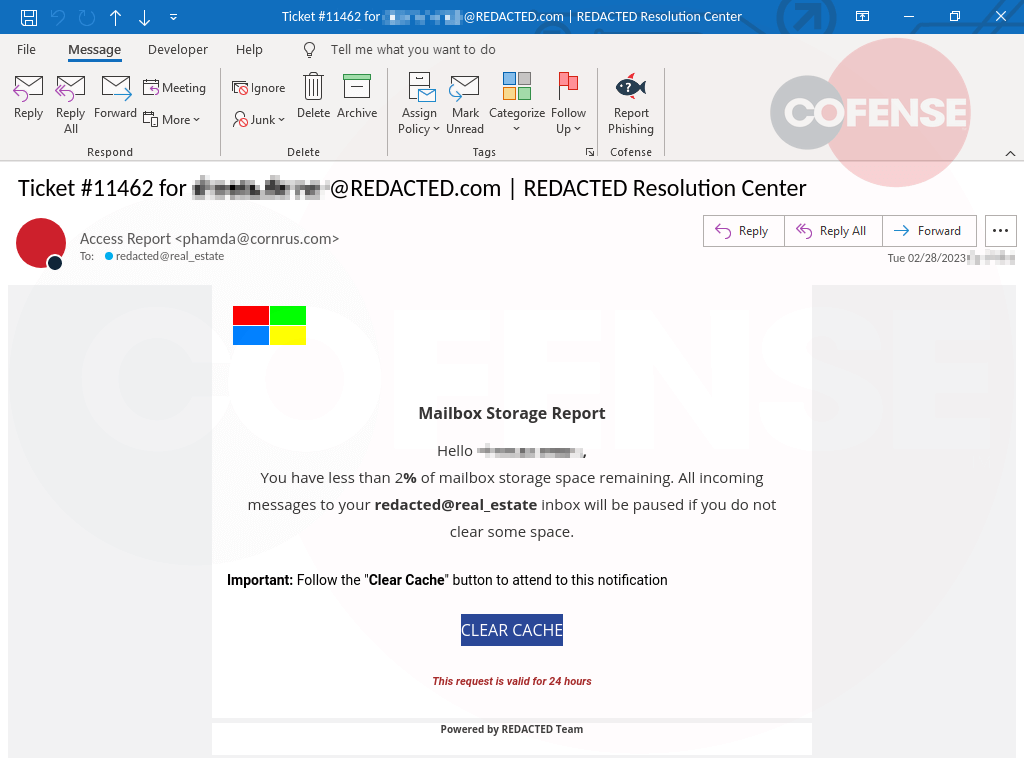
The most common tailored subdomain tactic in 2022 was the use of the organization’s primary domain, which is often identical to the organization’s name. A few campaigns incorporated the targeted recipient’s email username (the part before the “@” symbol in the email address) as well, but that was much more common as a parameter later in the URL than as part of the subdomain. Figure 2 shows a recent example of a credential phishing email that included a tailored subdomain. The entire email was customized with the name of the user and their organization, designed to imitate a legitimate message from an IT support department.
Figure 2: Example of a credential phishing email that included a tailored subdomain.
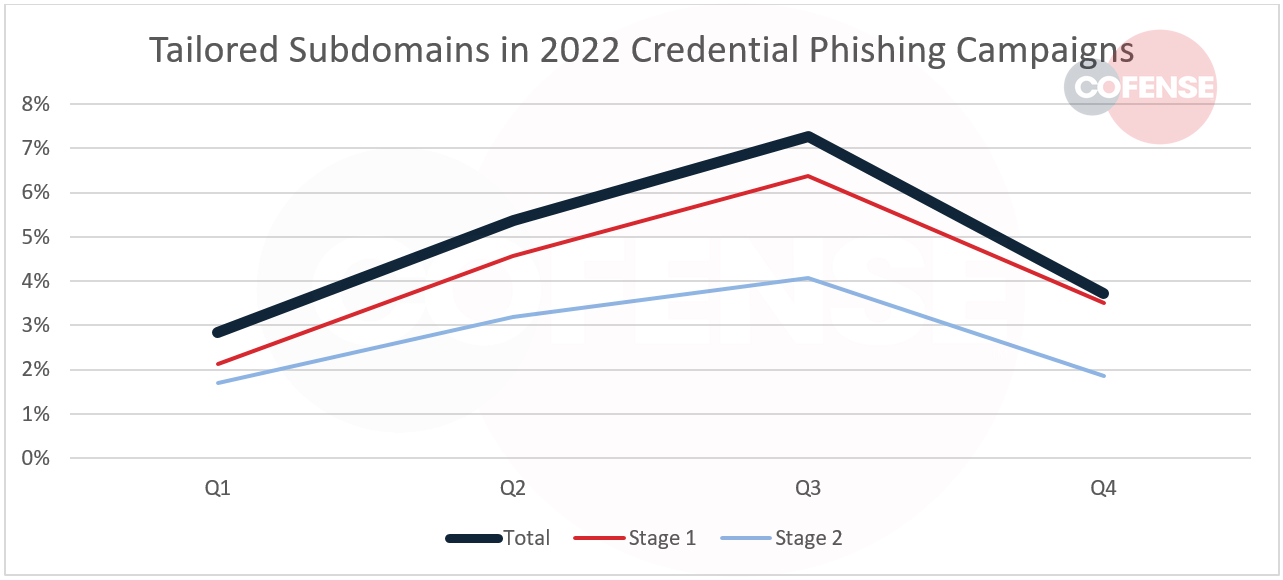
Figure 3 shows the usage of tailored subdomains among 2022 credential phishing campaigns that used subdomains. The share was 7% at its peak in Q3. As was the case with overall subdomain usage, tailored subdomains were more common in stage 1 URLs.
Figure 3: Percentage of tailored subdomains among campaigns that included subdomains.
In absolute terms, tailored subdomains are not used in an overwhelming number of campaigns. But they are common enough to warrant attention, especially since network defenders can easily craft rules to detect them based on the names, domains, and even usernames within their organization. Such rules may be particularly helpful with SEG configuration or email-focused threat hunting, since subdomain abuse in phishing emails is more prevalent at stage 1.
Campaigns Use Diverse Domains, URL Paths
Our past reporting has shown that other than a few legitimate services, credential phishing campaigns tend to use an enormous variety of domains, with each one only used a handful of times. Domains used with subdomains are similarly diverse:
- No single domain in 2022 was used in even 1% of campaigns with tailored subdomains.
- Legitimate services (even ones that allow threat actors to choose a subdomain) saw hardly any use.
- 77% of domains had a creation date available. Of those, 20% had been registered within 30 days of use with tailored subdomains. 57% were under between 1 and 20 years old, which suggests heavy use of already-established, hijacked domains.
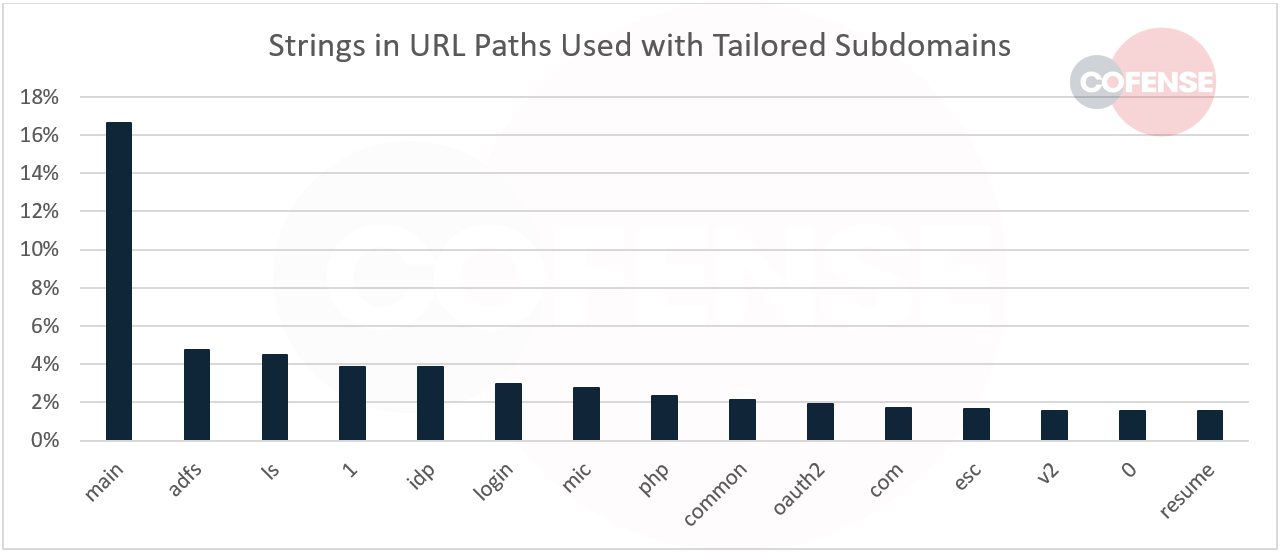
We also looked for common tactics in the URL path (the portion of the URL following the first “/” character) in campaigns using tailored subdomains. Most of them (68%) did not use a URL path at all. There was little consistency among the ones that did; Figure 4 shows the most common words in URL paths throughout 2022.
Figure 4: The 15 most common words in URL paths among credential phishing campaigns using tailored subdomains in 2022.
Only two tactics were relatively common, and neither of those tactics was represented by a common word or string. First, threat actors designed many of the malicious URLs to mimic the complex URLs used in legitimate enterprise authentication flows, with randomized strings. Second, some of the URL paths included the targeted user’s email address (sometimes in plain text, sometimes base64-encoded).
Recommendations
Although tailored subdomain are a relatively small part of the phishing threat landscape, network defenders should not overlook them. They may be more likely to fool users than generic phishing URLs, making them a more potent threat. However, they are more likely to be detectable as well. A few countermeasures could constitute easy wins for defenders:
- Create rules in SEGs, SIEMs, etc. looking for subdomains that include the organization’s name, primary domain, or any other prominent identifying terms, but which are not part of an already-known legitimate domain or service.
- Look for usernames and real names in subdomains. If automation capabilities allow for it, watch for names of all users; otherwise consider at least looking for the names of users in leadership positions or who have high levels of access.
- Consider similar rules that check URL paths for names, whether in plain text or encoded.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.