By Tej Tulachan, Cofense Phishing Defense Center
A noteworthy phishing campaign that abuses smart links LinkedIn redirects was recently observed by the Cofense Phishing Defense Center. This new, targeted campaign illustrates that while exploiting a well-known postal brand is nothing out of the ordinary, such phishing emails continue to go undetected by popular email gateways designed to protect end users.
Threat actors attempt to entice users into believing that the Slovakian Postal Service is requesting pending shipping costs. This is a very adaptable strategy due to smart links LinkedIn features and the variety of postal brands available. Threat actors abuse legitimate LinkedIn features with added unique alphanumeric variables at the end of the URL to redirect users to malicious websites. This is a clever tactic to bypass secure email gateways by abusing a commonly trusted source and falling for this attack can be avoided with users checking the embedded hyperlinks with extra precaution.
Email Body
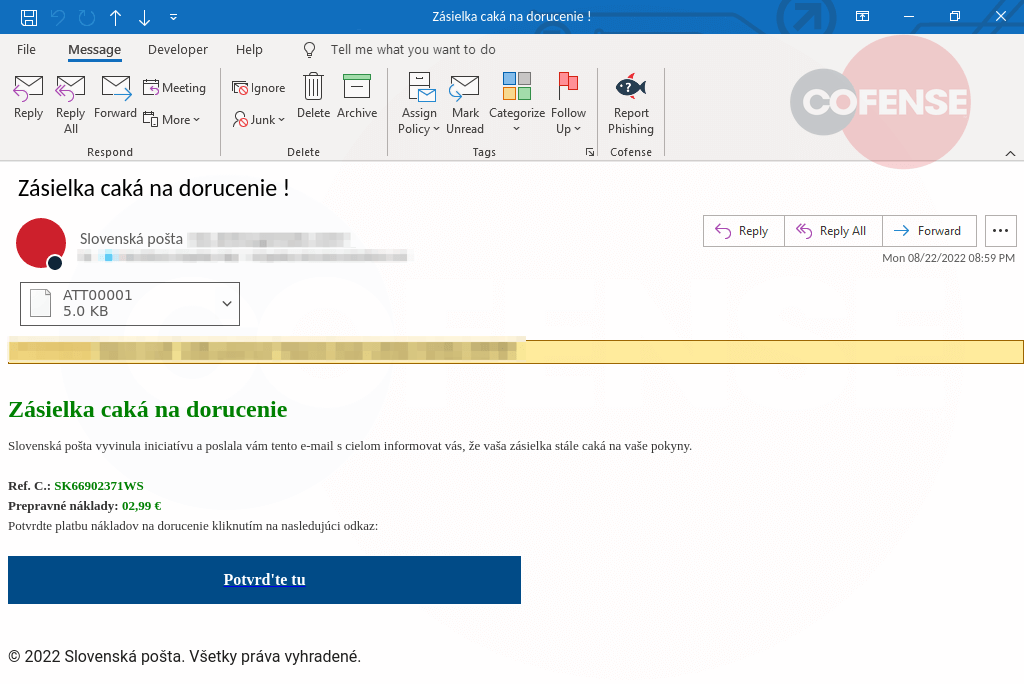 Figure.1: Phishing Email
Figure.1: Phishing EmailTranslation:
The shipment is waiting for delivery
Slovak Post took the initiative and sent you this e-mail to inform you that your shipment is still waiting for your instructions.
Ref. C.: SK66902371WS
Shipping costs: €02.99
Confirm payment of shipping costs by clicking on the following link:
Confirm here
As seen in Figure 1, the email was sent in Slovakian. Although we can see that the recipient has a shipment waiting to be delivered, the order can only be fulfilled with payment. Threat actors even added features to the email, including the fictitious reference number, to give the impression of legitimacy.
When the header information is examined more closely, it becomes clear that the threat comes from sis[.][email protected]. The threat actor is spoofing Slovenská Posta to appear authentic to the recipient.
As we examine more closely, we can notice that the message content contains the embedded smart link URL<hxxps://www[.]linkedin[.]com/slink?code=g4zmg2B6/> under “Confirm here”.
The LinkedIn “smart Link” feature allows users to redirect to legitimate websites to promote their website or advertisements. Threat actors, however, have different ideas and redirect users to malicious sites in an attempt to steal personal information. The threat actor’s choice of smart links LinkedIn is an effective way to get past the secure email gateway; many security protection tools are unlikely to block the URL. At the time of writing, the malicious URL in question is still live.
Phishing Page
Users are taken to the initial phase of this attack when they click the “Potvrd’te tu” button, as seen in Figure 1. The users are enticed to enter their bank card information to finalize the shipment order when they get to the payment page as seen in Figure 2.
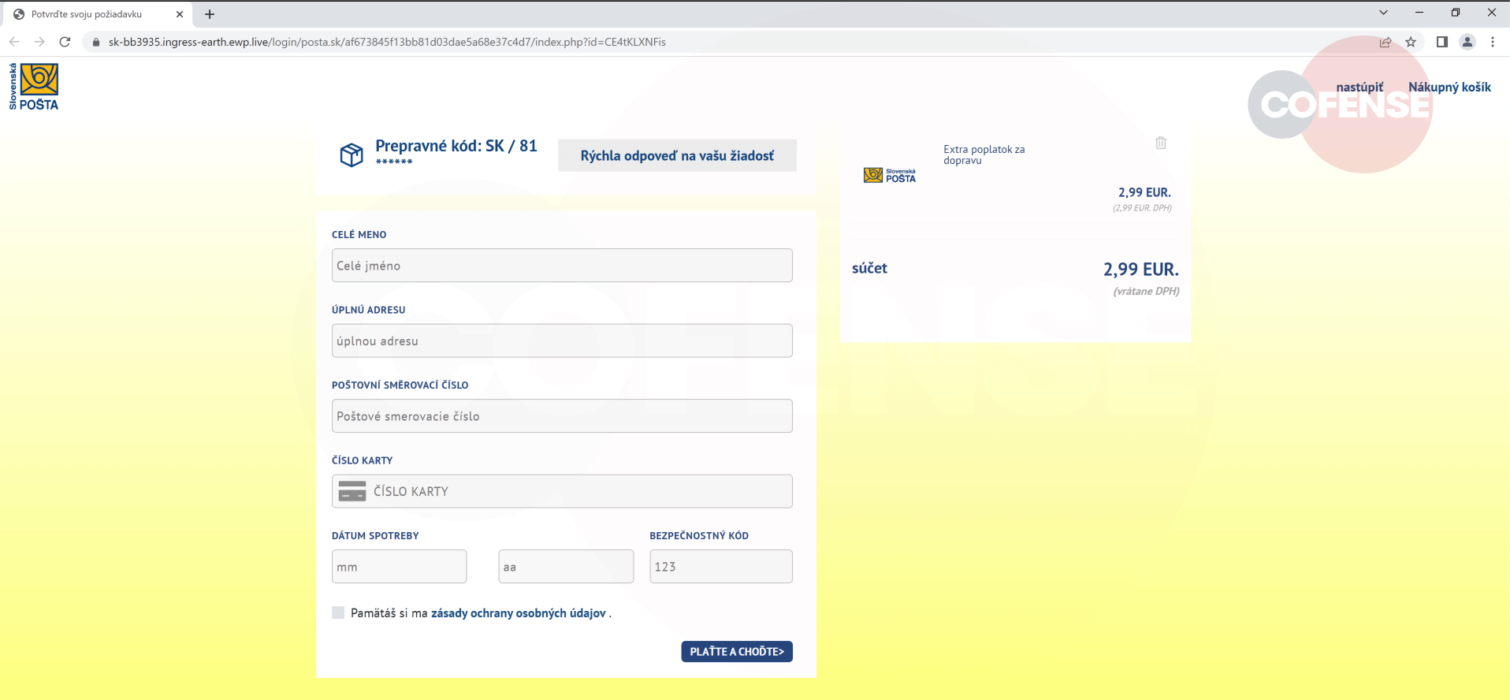 Figure.2: Phishing page
Figure.2: Phishing page In the final stage of the attack, the card details are entered and posted to the following address: hXXps://sk-1-b9833c[.]ingress-florina[.]ewp[.]live/login/cc/6c0924840f28f96026147e2cde8420af/card[.]php the user is redirected with a message informing them that their payment has been received and asking for a fake SMS code sent to their telephone number as illustrated in figure 3 (translated). Whatever digits are introduced in this page, the user will be redirected to a final fake confirmation page (figure 4), thereby deflecting suspicion.
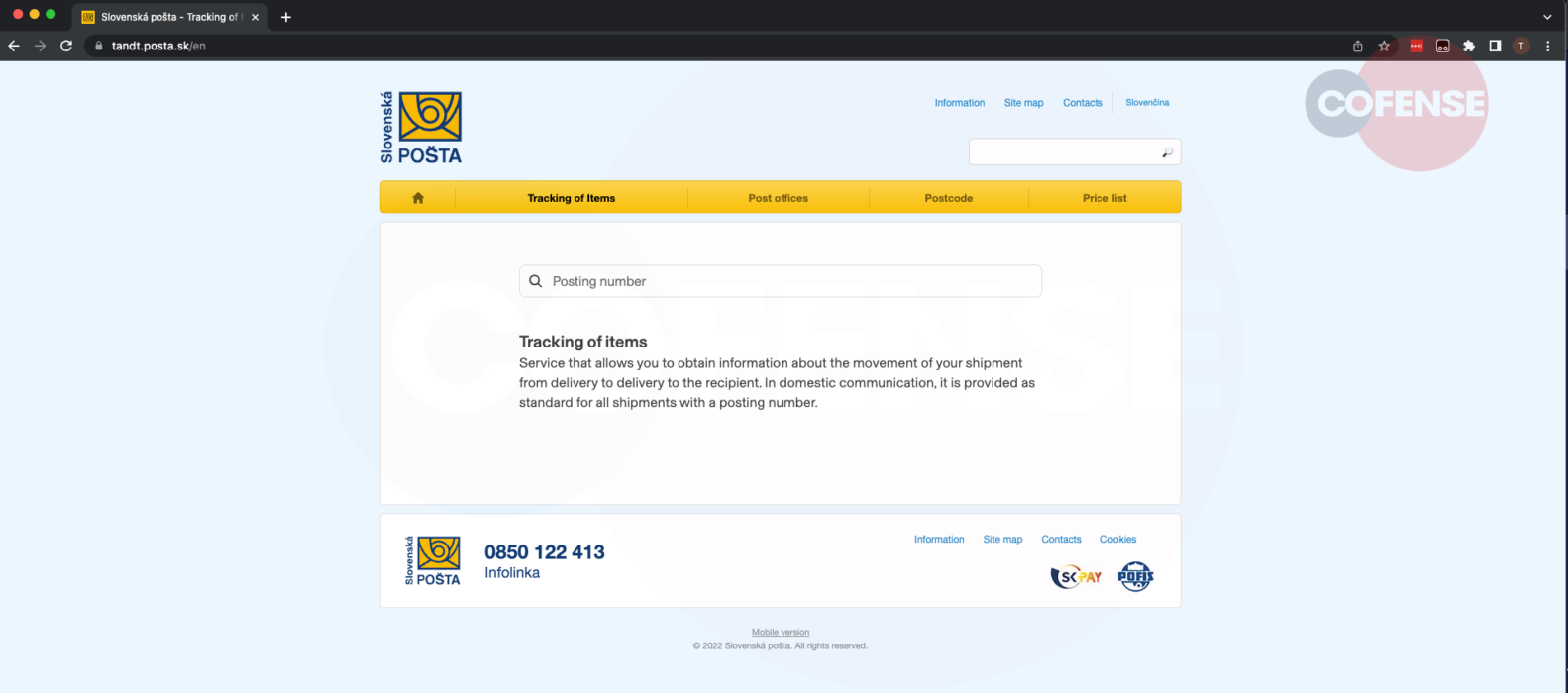 Figure.3: Submit Telephone number
Figure.3: Submit Telephone number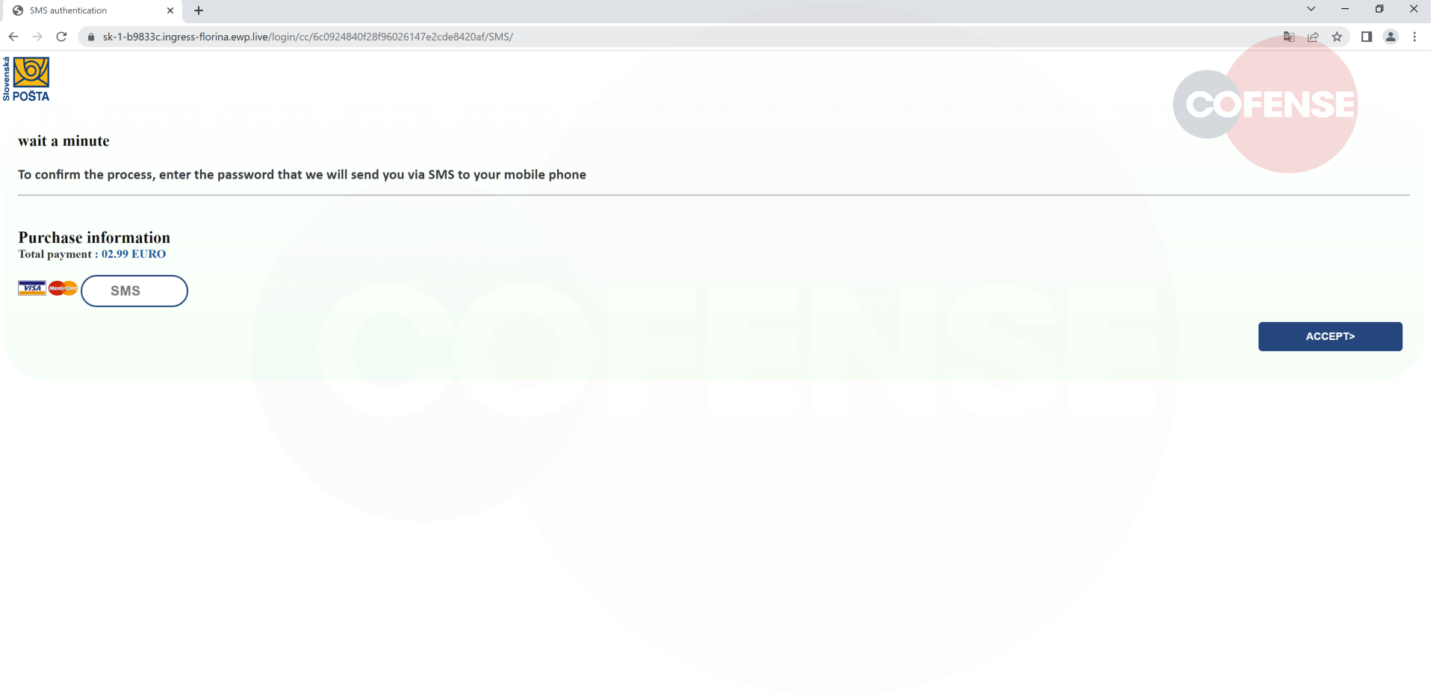 Figure.4: Fake confirmation
Figure.4: Fake confirmation The phishing landing page was intended to resemble the authentic Slovakian post, however, upon further examine, we found that the given URL does not correspond to the legitimate Slovakian Post URL https://tandt.posta.sk/en, as shown in Figure 5.
 Figure.5: Legit Slovak Post
Figure.5: Legit Slovak Post Due to a threat actor exploiting the official smart links LinkedIn service, the phishing page is still up and running. This campaign serves as an example of how secure email gateways can potentially be out maneuvered in the absence of an extra layer of defence provided by human sensors who can identify and report any odd emails and links that land in their inboxes.
| Indicators of Compromise | IP |
| hXXps://www[.]linkedin[.]com/slink?code=g4zmg2B6 | |
| hXXps://sk-1-b9833c[.]ingress-florina[.]ewp[.]live/login/cc/6c0924840f28f96026147e2cde8420af/index[.]php?id=BO0uBtRF3f7 | 63[.]250[.]43[.]136 |
| hXXps://sk-1-b9833c[.]ingress-florina[.]ewp[.]live/login/cc/6c0924840f28f96026147e2cde8420af/card[.]php | 63[.]250[.]43[.]137 |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.


