[vc_row][vc_column animation_iteration=”1″][mvc_infobox info_style=”mega_info_box_2″ info_opt=”show_icon” icon_size=”35″ icon_height=”75″ icon_radius=”15px” border_width=”2″ title_color=”#cd202c” font_icon=”fa fa-exclamation-triangle” icon_color=”#cd202c” border_clr=”#dd3333″ info_title=”Gateways Bypassed” title_size=”25″ css=”.vc_custom_1585945659827{margin-top: 20px !important;margin-bottom: 30px !important;}” hoverclr=”#cd202c” icon_bg=”#ffffff” hoverbg=”#ffffff”]
Microsoft 365 EOP
[/mvc_infobox][/vc_column][/vc_row][vc_row][vc_column][vc_column_text c_id=”.vc_1635881434305″]Recently, the Cofense Phishing Defense Center observed a wave of phishing attacks targeting TSB banking customers in the UK. We found these consumer-oriented phishing emails in corporate environments, after the malicious messages made it past perimeter defenses.
The convincing emails aimed to harvest an unsuspecting victim’s email, password, mobile numbers, and the “memorable information” used in two-factor authentication. If someone were to bite on the phish, they would be open to follow-up phone scams or the complete takeover of their bank account and credit cards.
Most UK banks implement two-factor authentication. They require users to set a standard password and a piece of memorable information, which users authenticate with their user name and password. Users are then asked to provide three random characters from their memorable information. This does two things to help improve the security of your bank account:
- It can help mitigate against man in the middle attacks, as any intercepted data would only reveal partial fragments of the memorable information.
- If a user’s email address and password combination has been leaked online, it provides an extra barrier for attackers attempting to access their accounts.
Again, if successful this phish could help the attacker evade these extra controls. Here’s how it works:
Email Body:
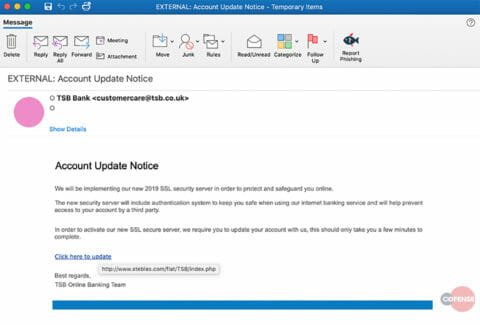
The attacks begins with an email purporting to be from the TSB customer care team, informing the customer that a new “SSL server” has been implemented to prevent access to customer accounts by third parties. It then asks the user to update their account information by clicking on the conveniently placed hyperlink.
Fig 1. Phishing Email
Headers:
To add authenticity to the attack, the threat actors have spoofed the sending information to make the email appear to come from the sender customercare[@]tsb[.]co[.]uk If we correlate this with the message ID, we can see that it actually originated from the ttrvidros[.]com[.]br a Brazilian registered domain.
From: TSB Bank <customercare[@]tsb[.]co[.]uk> To: "MR, Example" <[email protected]> Subject: EXTERNAL: Account Update Notice Thread-Topic: EXTERNAL: Account Update Notice Thread-Index: AQHVJzUy0rKRdi+45UWU8FPBrgSqiQ== X-MS-Exchange-MessageSentRepresentingType: 1 Date: Thu, 20 Jun 2019 06:55:28 +0000 Message-ID: <5630c1ff905b65891e435ec91b8a1390[@]www[.]ttrvidros[.]com[.]br> Content-Language: en-GB
Fig 2. Header Information
Phishing Page:
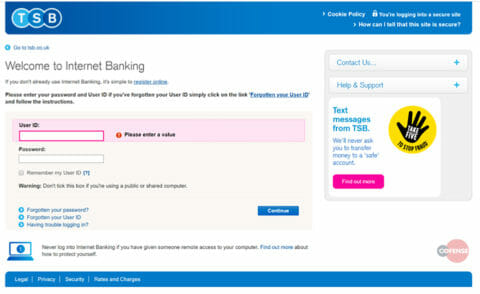
The malicious page shown below on fig3 is almost identical to TSB online banking portal. The first page is directed to ask for a User ID and password.
Fig 3. Phishing Page 1
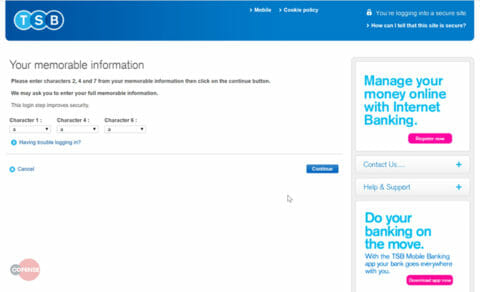
The victim is then asked to supply characters from their memorable information. This is typically a word that is memorable to the user and six characters or longer, usually a pet’s name, mother’s maiden name, or a favorite city or sports team. It is standard practice to only provide three characters of your memorable information. However, this is just a clever ruse to gain the confidence of the victim.
Fig 4. Phishing Page 2
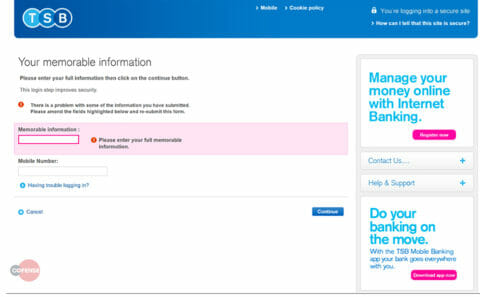
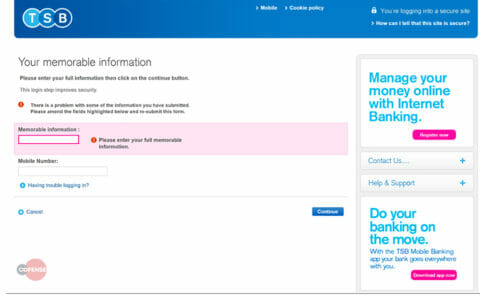
The user is then redirected to a fake error page that states, “There is a problem with some of the information you have submitted. Please amend the fields below and resubmit this form.” Afterward, the form asks the victim for the full memorable information and the mobile phone number. Armed with the victim’s user-ID, password, memorable information, and phone number an attacker can easily gain access to the victim’s bank account and credit cards through the online portal—or perhaps more worryingly, they can utilize this information to launch a social engineering campaign over the phone, commonly referred to as vishing (Voice Phishing).
Fig 5. Phishing page 3
Gateway Evasion:
This threat was found in an environment running Microsoft Exchange Online Protection (EOP) which provides built-in malware and spam filtering capabilities it is intended to screen inbound and outbound messages from malicious software spam transferred through email.
Learn More
75% of threats reported to the Cofense Phishing Defense Center are credential phish. Protect the keys to your kingdom—condition end users to be resilient to credential harvesting attacks with Cofense PhishMe™, which among many training scenarios offers an “Account Update Notice” phish to prepare for the type of credential attack examined in this blog post.
Quickly turn user reported emails into actionable intelligence with Cofense Triage™. Reduce exposure time by rapidly quarantining threats with Cofense Vision™. Cofense is the only company that combines a global network of 30 million people reporting phish with advanced AI-based automation to stop phishing attacks fast. Learn more about our holistic phishing detection and response solution here.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks.
[/vc_column_text][/vc_column][/vc_row]