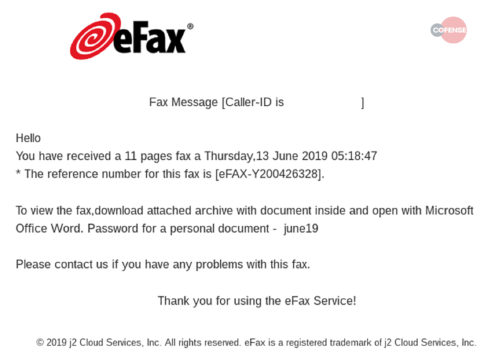
Cofense IntelligenceTM analyzes millions of emails and malware samples each day to alert organizations to emerging phishing threats. Thanks to our expansive view of the threat landscape, we recently were able to discover and investigate a campaign impersonating eFax that appeared to have an attached Microsoft Word document. The attachment was a .zip archive which contained a .xls Microsoft Excel spreadsheet. This spreadsheet included an Office macro which, when enabled, was used to download and execute two malicious executables: samples of Dridex and Remote Manipulator System Remote Access Tool (RMS RAT).
What’s notable: By delivering a banking trojan and a RAT, the threat actors are able to use the banking trojan purely for credential stealing via browsers and use the RAT for more complex management of the infected computer. Dridex may be able to handle some of the machine management tasks, but by using RMS RAT and Dridex for separate purposes threat actors can more efficiently accomplish their tasks. And having both available provides a backup communication channel in case one of the malware families is detected and removed.
RMS RAT Features
RMS RAT is a legitimate remote access tool appropriated for malicious use by threat actors. RMS RAT has a large number of features that include logging keystrokes, recording from the webcam or microphone, transferring files, and manipulating Windows Task Manager and other Windows utilities. This multi-featured tool allows for significant control of a compromised computer as well as multiple methods of information gathering. Due to its legitimate origins and usage of legitimate components, not all endpoint protection suites will immediately detect this tool as malicious, which allows threat actors more time to establish a foothold in the infrastructure.
Dridex Web Injects
Banking trojans often target a large number of websites and use different kinds of scripts for different targets. Some banking trojans will even share the same scripts and targets with other banking trojans. When a victim on an infected machine visits one of the targeted websites in an internet browser, the script will be “injected” into the browser. This allows the threat actor to steal information entered, redirect traffic, bypass multi-factor authentication, and even provide additional “security questions” to obtain information from the victim. In this case, the web injects used by Dridex were unusual because of both the large number of possible web inject scripts and the fact that some of the web injects were labeled as being from the Zeus banking trojan.
There are three types of web injects used in this case. The first type is used to hide or display content on certain web pages, making it possible to insert additional requests for personal questions used to verify banking accounts. The second type monitors the URLs visited by the browser and downloads additional files; the web injects labeled as Zeus fall in this category. Both of these web injects come hard coded into the original malicious binary. The third type of web inject is downloaded from a remote host and often has more capabilities, including greater information-gathering capacity.
Web injects in this sample of Dridex target a variety of websites:
- The first set targets crypto currency websites such as coinbase[.]com and banking websites such as hsbc[.]co[.]uk and synovus[.]com. The web injects for these targets are downloaded from the same command and control location, 144[.]76[.]111[.]43.
- A second set of web injects targets e-commerce websites, including paypal[.]com and bestbuy[.]com, and is sourced from a different location: akamai-static5[.]online. The threat actor’s use of this particular domain name is clever because it is similar enough to an Akamai network domain name that the domain might not be reported because it looks legitimate.
- The final set of web injects are tagged as “Zeus” injects. The use of these injects is particularly unusual because several of the targeted websites overlap with those in other web injects, such as paypal[.]com and amazon[.]com.
By using multiple types of web injects, and in some cases duplicating websites of other web injects, the threat actors have a wide variety of possible targets at their disposal. Using both old and new web injects can also help threat actors target information even when the structure of the webpages’ URL has changed over time.
Threat Results and a Look Ahead:
The dual-pronged attack in this case provided the threat actors with multiple methods of compromise, access to data, and some resistance to traditional endpoint protections. RMS RAT provided remote access, key logging, and credential stealing. And using different types of web injects enabled threat actors to utilize some of the features of Zeus to improve the capabilities of Dridex. Each different type of web inject also made use of a different command and control location to provide information, which can help make the threat actor’s infrastructure more resilient.
Knowing all of the possible threats in combination rather than those seen individually can help organizations prepare for and defend against threats. Training employees to spot and report possible phishing messages can help stop malware from making it to an endpoint and prevent threat actors from ever establishing a foothold.
Learn More
See how Cofense Intelligence analyzes and processes millions of emails and malware samples daily so security teams can easily consume phishing-specific threat intelligence. Discover how to proactively defend your organization against evolving phishing attacks and the latest malware varieties.
Appendix:
Table 1: List of potential web inject source
| Web Inject Sources |
| hxxps://144[.]76[.]111[.]43:443/5/amex_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/5/bbt_biz_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/5/bbt_corp_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/5/bmo_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/5/bnycash_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/5/bremer_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/5/pnc_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/5/scotiabank_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/5/tdbank_tdetreasury_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/510/tiquani_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/amama_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/amunba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/atonbu_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/bacana_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/bahaba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/bokafi_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/bomobo_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/buliba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/camaba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/camaci_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/camana_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/cibaca_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/cobaba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/cobuba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/emriba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/ewaba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/facosa_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/famaba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/finiba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/fumaba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/hacaba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/hasaba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/hasaba_uk_pers_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/iboaba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/inruba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/irisoba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/katata_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/lakala_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/lemiba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/madaba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/magaba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/matawa_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/mecoma_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/moboma_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/osv_cetiba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/osv_fasaba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/osv_sabatu_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/osv_tobipu_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/pawaba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/peniba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/pocoba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/povaba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/rabaca2_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/rabaca_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/rasaba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/satara_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/secaba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/sigaba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/socoba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/synova_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/tadaba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/todoba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/ubatra_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/unbaba_l4R5Ej69o91Bc3ja/ |
| hxxps://144[.]76[.]111[.]43:443/520/wabaca_l4R5Ej69o91Bc3ja/ |
| hxxps://akamai-static5[.]online/appleadmin/gate[.]php |
| hxxps://akamai-static5[.]online/bestbuyadmin/gate[.]php |
| hxxps://akamai-static5[.]online/costcoadmin/gate[.]php |
| hxxps://akamai-static5[.]online/ebayadmin/gate[.]php |
| hxxps://akamai-static5[.]online/neweggadmin/gate[.]php |
| hxxps://akamai-static5[.]online/ppadmin/gate[.]php |
| hxxps://akamai-static5[.]online/samsclubadmin/gate[.]php |
| hxxps://akamai-static5[.]online/walmartadmin/gate[.]php |
| hxxps://bustheza[.]com/lob[.]php |
| hxxps://cachejs[.]com/lob[.]php |
| hxxps://46[.]105[.]131[.]77:443/B88U86giIPyD55RK/ |
| hxxps://46[.]105[.]131[.]77:443/ehf9i7ywh5kdyu50/ |
| hxxps://46[.]105[.]131[.]77:443/xobj6j20x84lhk3x/ |
Table 2: Command and control hosts (C2)
| RMS RAT C2 |
| 217[.]12[.]201[.]159:5655 |
| Dridex C2 |
| hxxps://71[.]217[.]15[.]111:443/ |
| hxxps://97[.]76[.]245[.]131:443/ |
| hxxps://24[.]40[.]243[.]66:443/ |
| hxxps://159[.]69[.]89[.]90:3389/ |
| hxxps://159[.]89[.]179[.]87:3389/ |
| hxxps://62[.]210[.]26[.]206:3389/ |
Table 3: Payload locations
| Office Macro Payloads |
| hxxp://topdalescotty[.]top/filexxx/wiskkk[.]exe |
| hxxp://topdalescotty[.]top/filexxx/wotam[.]exe |
All third-party trademarks referenced by Cofense™ whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks.