Phishing websites are designed to steal usernames, passwords, and additional PII when unsuspecting victims are enticed to log in. Credential phishing intelligence is used to hunt, detect, and block access attempts to spoofed sites as well as to raise awareness about the latest tactics, techniques, and procedures used with credential and malware phishing campaigns.
The new credential phishing feature from PhishMe Intelligence™ delivers additional information to help defend against credential-gathering attacks. The credential phishing intelligence is available via the PhishMe Intelligence API and portal.
This blog is the first in a series about credential phishing in the enterprise.
Credential Phishing and Office 365
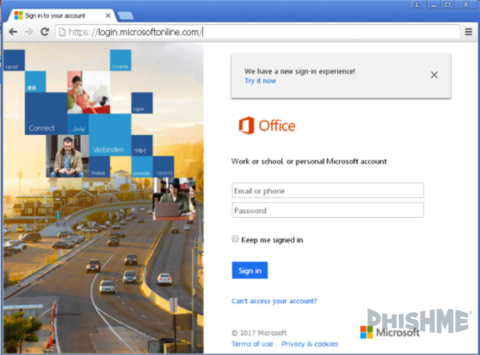
Microsoft Office 365 was released in 2011 and the has become hugely popular among enterprises both large and small. For those in a workplace that has fully-integrated Office 365, it feels as if you use that one password to log in to just about everything using any device. It all just works seamlessly. This is what the Office 365 login page looks like on Microsoft’s site https://login.microsoftonline.com. (Figure 1).
Figure 1 – Real Office 365 Login Page
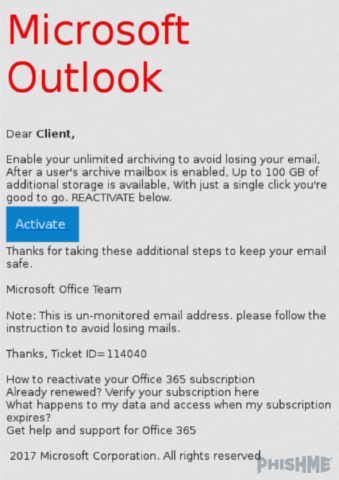
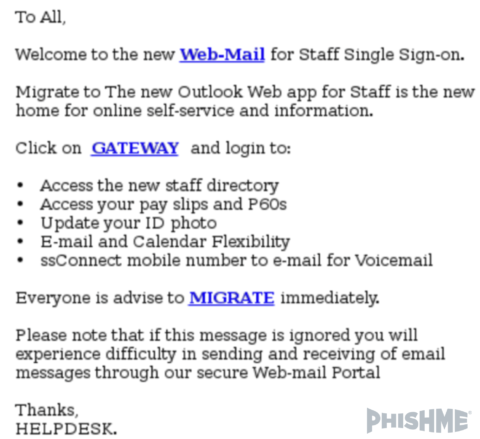
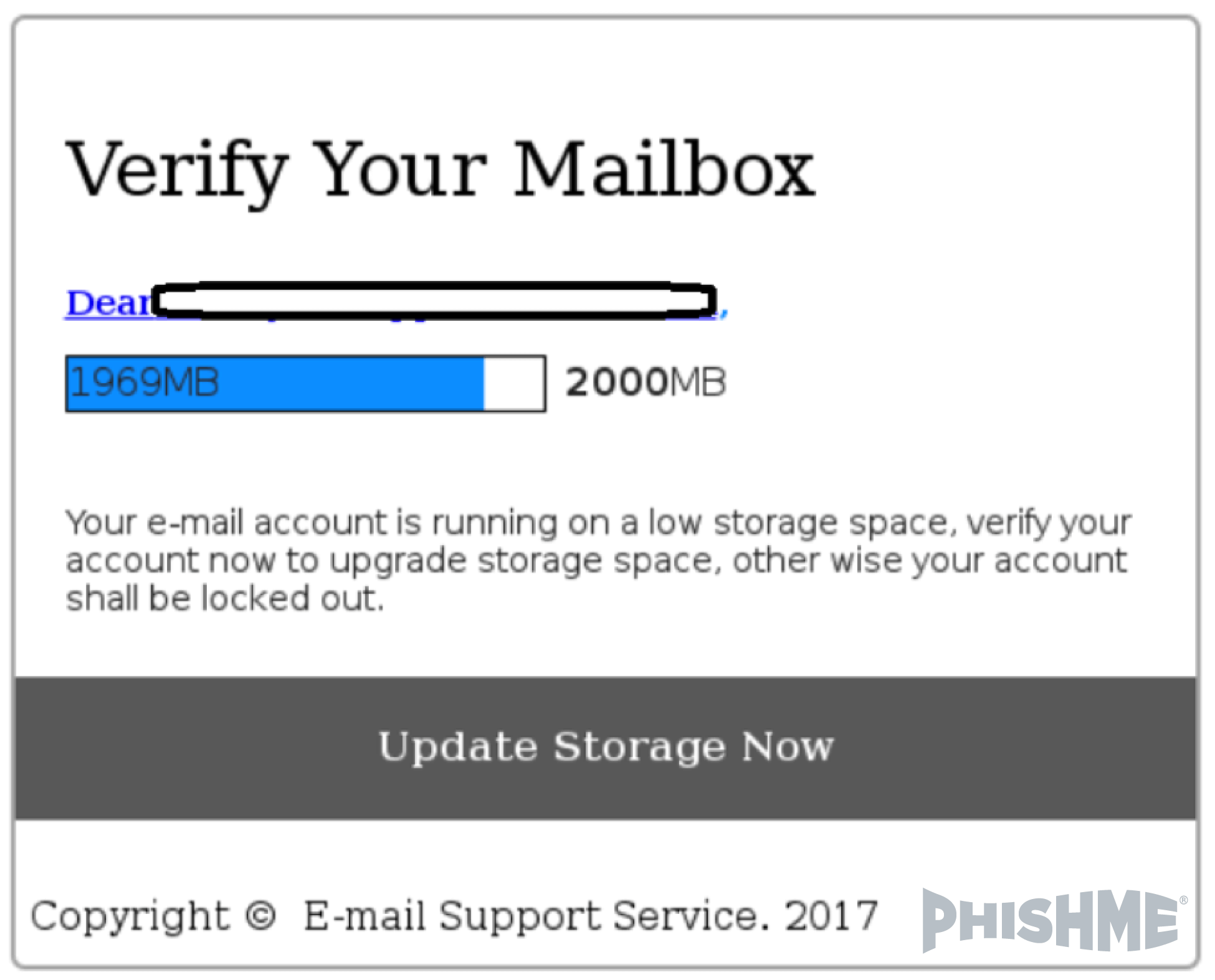
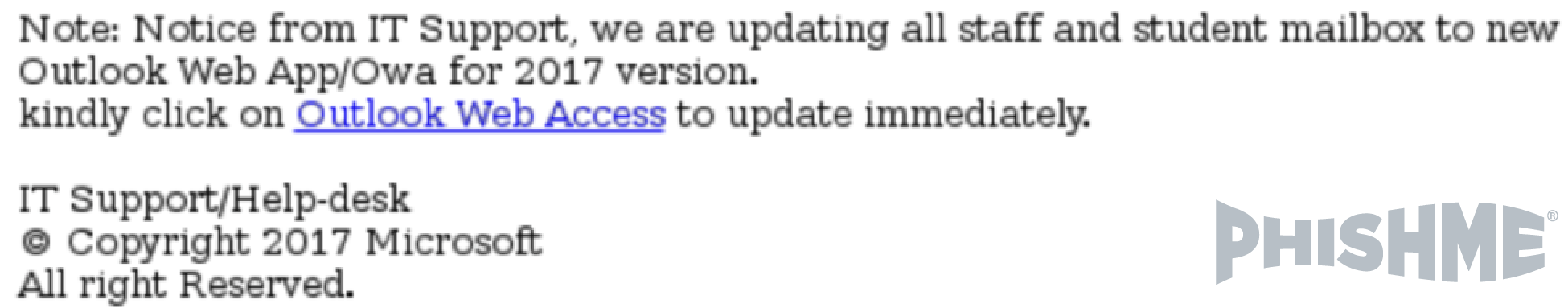
Outlook 365 users are reporting suspicious messages to PhishMe® that contain links a page that looks like figure 1, but are hosted on compromised or fraudulent sites. As seen below in figures 2-5, are some examples of the suspicious messages that enterprise employees are receiving:
Figure 2 – Suspicious O365 Message (1 of 4)
Figure 3 – Suspicious O365 Message (2 of 4)
Figure 4 – Suspicious O365 Message (3 of 4)
Figure 5 – Suspicious O365 Message (4 of 4)
All of these messages are designed to look legitimate – like something from IT – and mimic the Office 365 login page. But in reality, they deliver the unsuspecting user to a fraudulent site to steal their information. This type of phishing has been growing rapidly. The examples shown in Figures 2-5 were captured within only 90 minutes. Over the past month PhishMe has detected credential phishing pages hosted on over 1,100 hostnames, which have likely distributed via tens of thousands of email messages. Microsoft’s own Security Intelligence Report reveals that there has been a dramatic increase in the number of account sign-ins attempted from malicious IP addresses.
The fallout from a successful Office 365 credential-based attack is so large that measuring it has become a data analytics problem. Estimating the extent of the damage is near impossible. Because many of victims don’t know they have entered their credentials on a fake site. If compromised, a threat actor could be in your system for a long time before you discover a breach. The time between the initial intrusion and detection of compromise, known as dwell time, is currently estimated to be 49 days (seven weeks).
New and different
While the attacks described above have been appearing for years, we’ve seen some new examples that seem a bit different. In these examples, the attackers are exploiting features of Office 365 as part of their phishing campaign.
Office 365 Forms
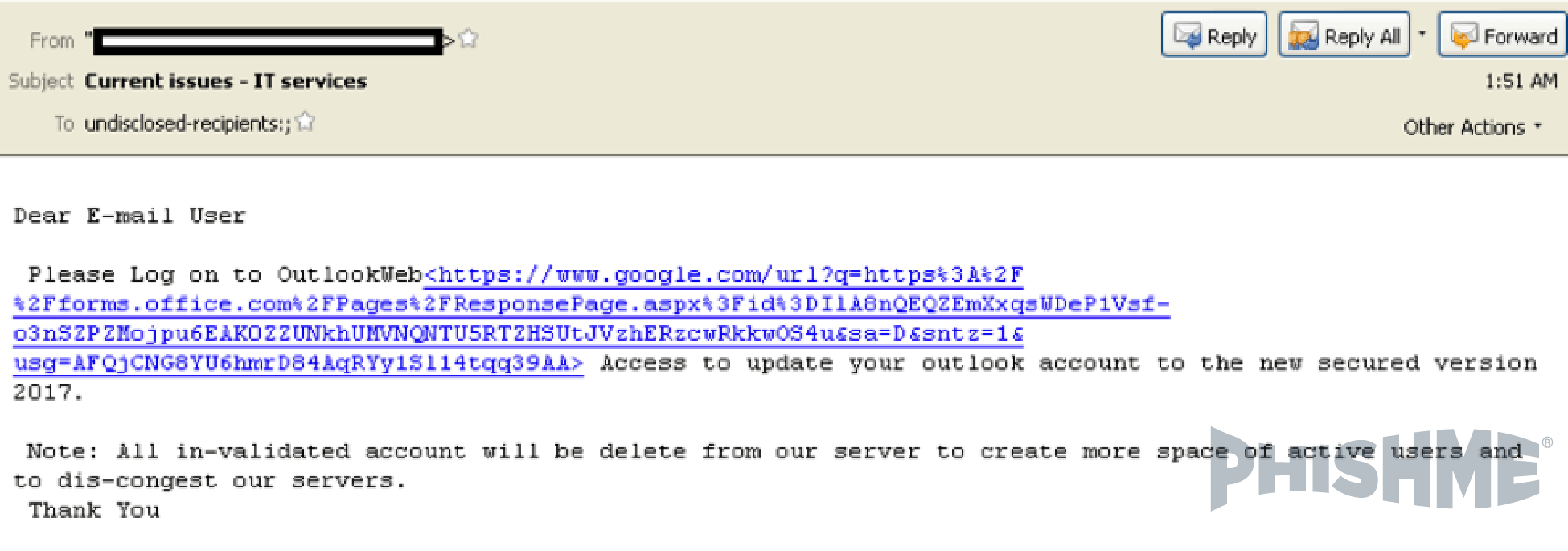
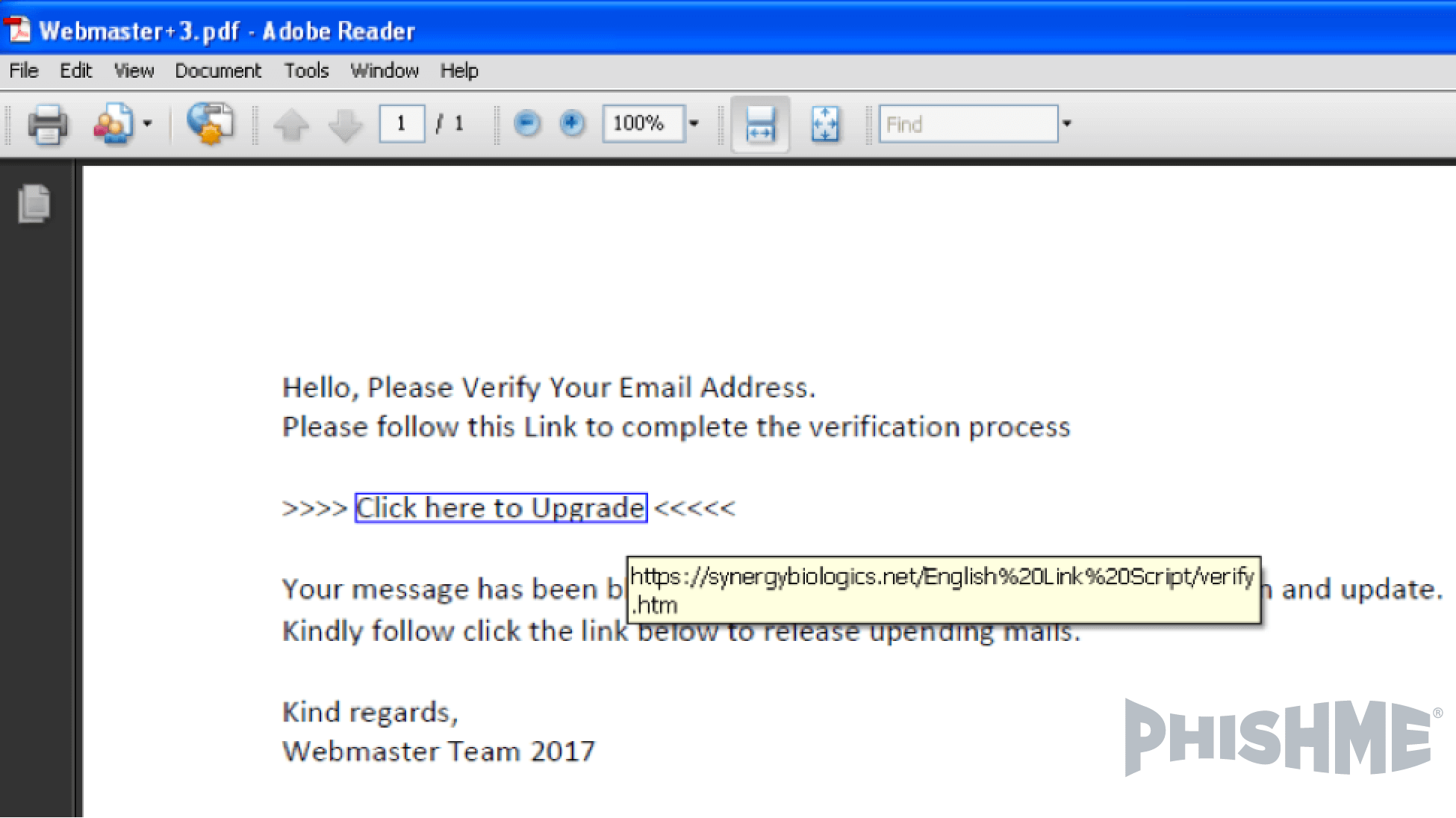
In the first example an attacker uses the Office 365 Forms app to create realistic phishing pages that are hosted on a Microsoft domain. Figure 6, below, shows a message linked to Google.com to redirect to Forms[.]Office.com:
Figure 6 – Message contains link to Google.com URL
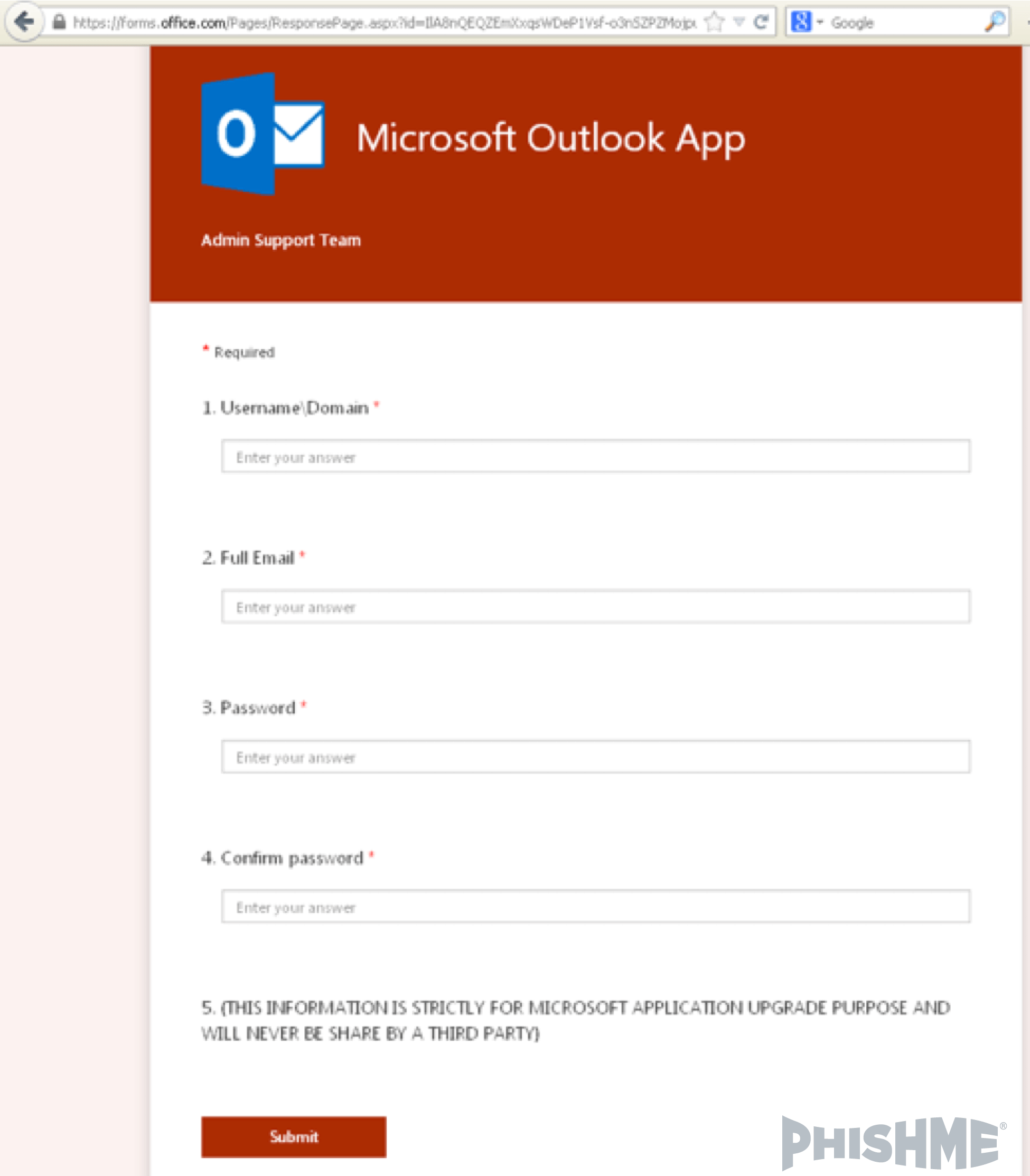
When that link is clicked, the phishing form is displayed (figure 7) on a domain that just about any IT department would be reluctant to block.
Figure 7 – Office.com form reached from link in phishing message
URL Shortening
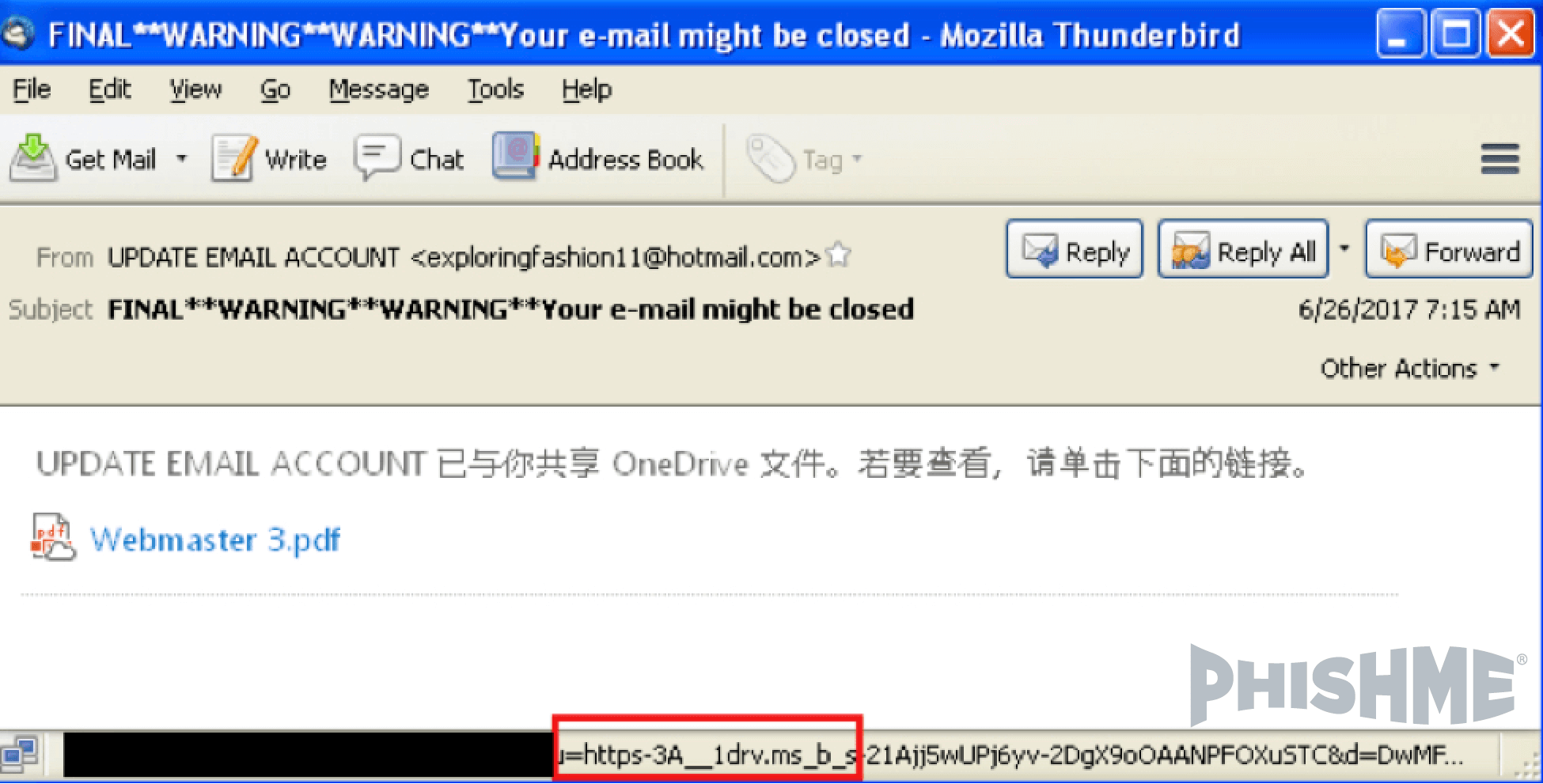
To make things more confusing, consider that Microsoft conducts URL shortening using the domain name 1drv[.]ms. PhishMe customers are reporting phishing messages that contain URLs on that domain that then redirect to Onedrive[.]Live.com to load a PDF document that contains yet another link. As you can see in figure 8, this message contained a shortened link that slipped through technological defenses:
Figure 8 – OneDrive Shortened Link
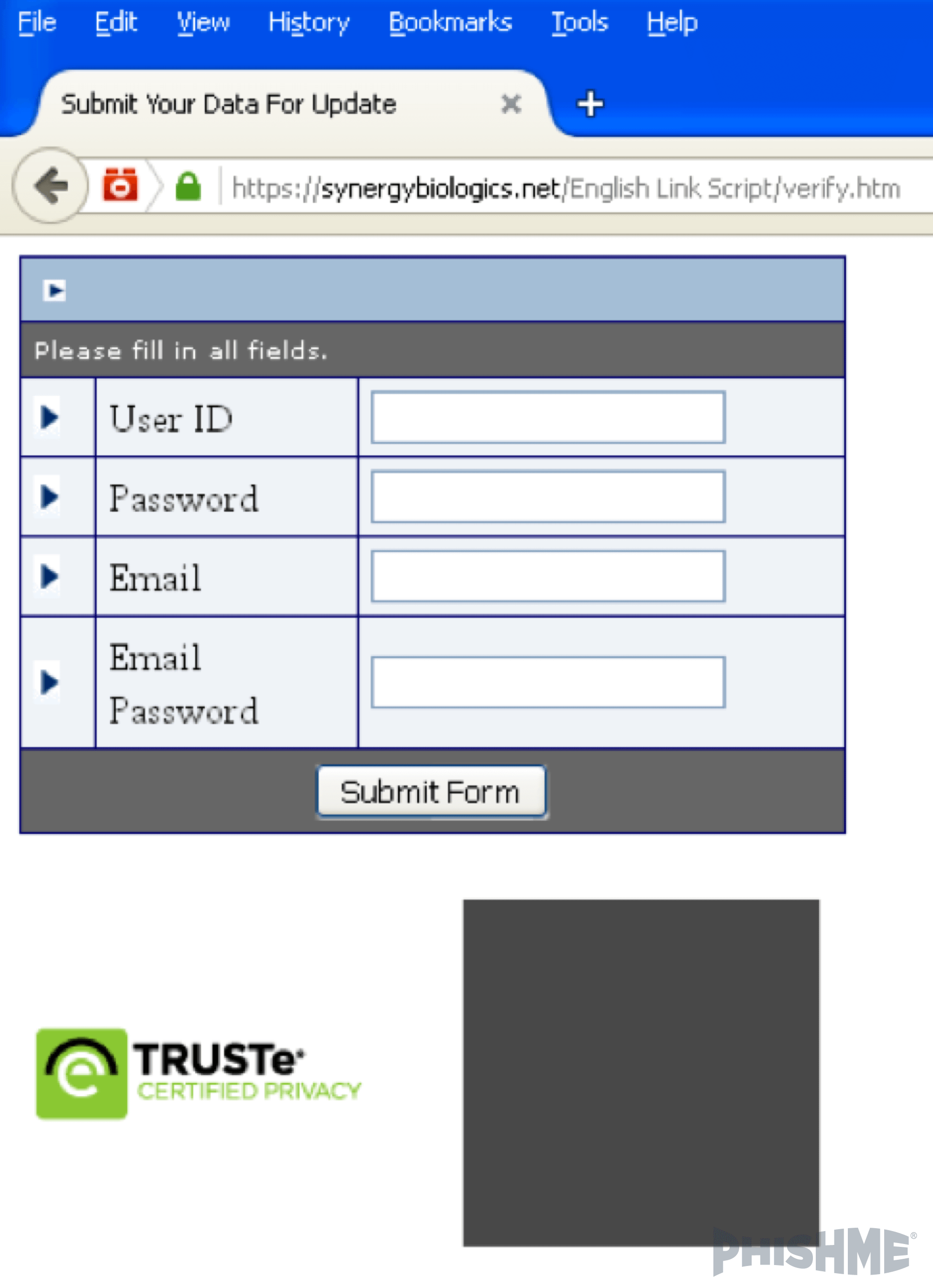
The resulting PDF (figure 9) can open in the browser and deliver a link to a compromised site that hosts a phishing page.
Figure 9 – PDF from OneDrive with Malicious Link
By the time the victim reaches the somewhat-generic page below (figure 10), they have clicked through at least three trusted services.
Figure 10 – Final Destination from Original OneDrive Link
Personalized Email
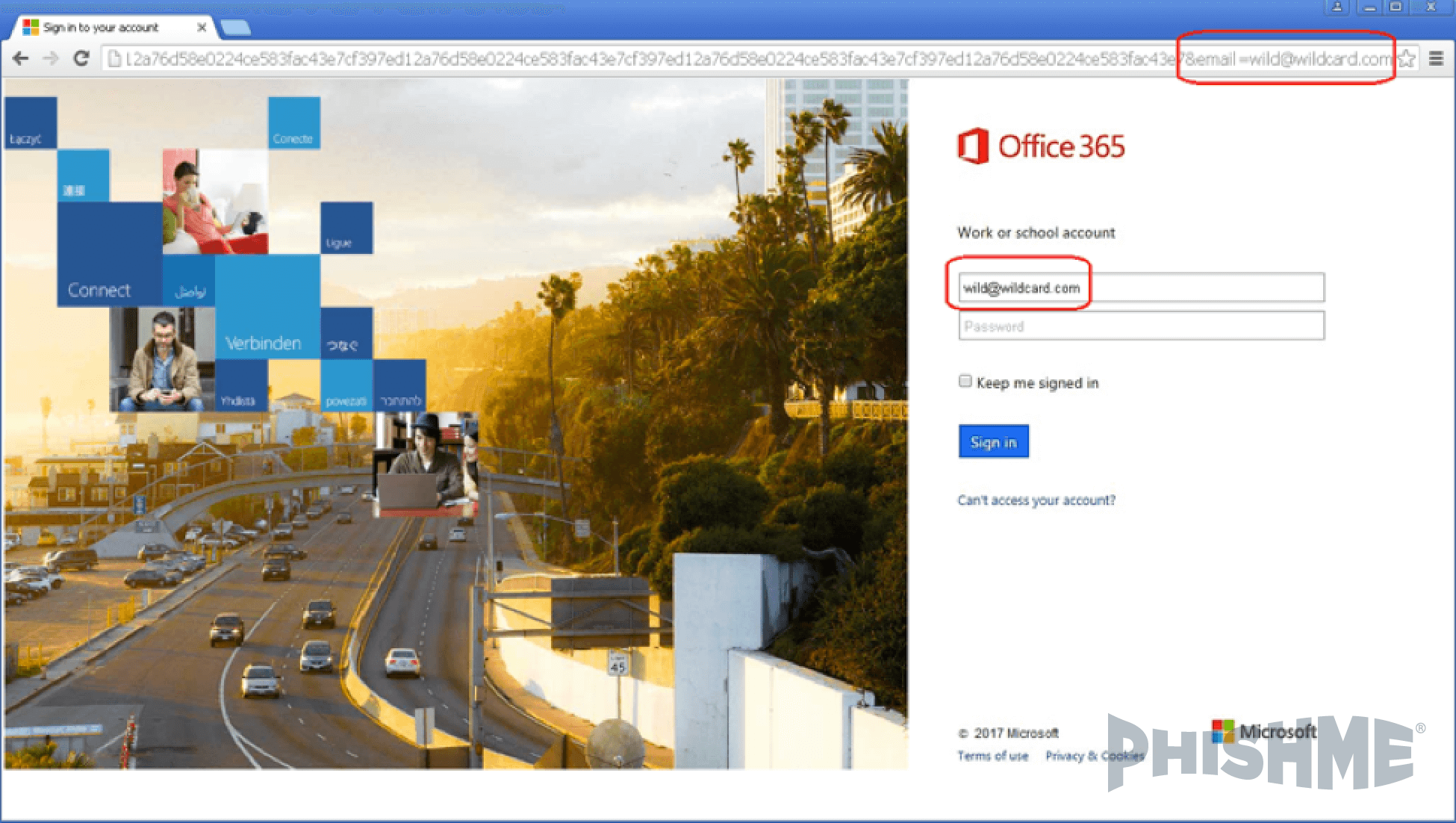
Many of the phishing messages are created using a template that inserts the recipient’s email address into the URL that the victim is enticed to click. Seeing a personalized link, the victim is made to feel that the message was built just for them so that they can log in as normal and resolve the supposed problem with their account. Other, similar functionality can extract the domain name from the recipient’s email address and display it in a large type, with an uppercase letter, to further spoof a login page for that company.
To reach the page in figure 11, we clicked a link containing the test email address [email protected]’ in the query string, as follows:
hxxp://www.medicalinnovation[.]it/wp-admin/user/365?wild@wildcard[.]com
Though the landing page was on a different domain, the address was passed along so that it remained a part of the URL and was displayed on the page, already conveniently completing half of the form:
Even though the above example above does not represent a spear phish per se, we do see soft targeting and targeting of employees at specific large companies. Soft targeting involves the use of social media or public information about a company to tailor the recipients, the message templates, and the landing pages to be attractive to those in certain roles at a company.
What can you do?
- Use PhishMe Simulator™ and the PhishMe Reporter® plugin for Outlook to condition your employees to recognize and report suspicious messages to your incident response team.
- Employees can also fall victim to phishing attacks that compromise PCs with malicious software. Use PhishMe Intelligence™ to identify when users go to credential phishing sites or their machines exhibit indicators of compromise with malware.
- Enable two-factor authentication on all employee accounts.
- Once a credential phishing message is detected:
- Delete other related messages received within your enterprise
- Check perimeter devices for connections to the phishing URL
- Adjust controls to block similar messages by the URL and its host and/or domain, by the subject line, and/or by the sending IP address
- For employees who fell victim to a credential phish, force password re-sets and provide additional training about phishing attacks. Consult Microsoft’s technical support pages “How to determine whether your Office 365 account has been compromised” and “How to fix a compromised (hacked) Microsoft Office 365 account“.
Learn More
Don’t miss out on another threat! Sign up for PhishMe® Threat Alerts today and receive updates on new and emerging phishing and malware threats, completely free.