Author: Max Gannon, Intelligence Team
Threat actors use many methods to avoid detection and complicate the analysis of their credential phishing pages and campaigns. Many of these are built into the kits that threat actors purchase, while others must be manually implemented. This report covers some tactics, techniques, and procedures (TTPs) used by threat actors in phishing kits to prevent and delay detection of their credential phishing pages, email phishing campaigns, and related resources.
Embedded Content
One of the most common tactics that threat actors use to evade detection of their phishing emails is customizing the content embedded into their email phishing campaigns so that the links leading to credential phishing pages are, in some manner, disguised, obfuscated, or layered behind other content. Some of the most common methods of customizing this content are using links to legitimate file-sharing platforms, abusing open redirects, and embedding QR codes.
Legitimate Hosts
Threat actors using legitimate sites to evade detection is nothing new and has been going on since the early days of credential phishing and malware delivery. While some legitimate pages are used to directly host malware or credential phishing pages, this is rare, as those types of resources are typically taken down by the legitimate company in short order. Instead of directly hosting the content, threat actors often embed links to the malicious credential phishing pages in legitimate sites hosted on locations such as DocuSign, Google Docs, Canva, and Zoho. This topic has been covered in depth by Cofense in several relevant 2025 Strategic Analyses, such as one on “Threat Actors Abuse Trust in Cloud Collaboration Platforms” and another on “Threat Actors Exploit Government Website Vulnerabilities for Phishing Campaigns”.
Redirects
Threat actors frequently make use of open redirects using legitimate services such as Google AMP, which can be used to redirect victims to credential phishing websites without the user knowing they are being redirected. Some of the most recently abused services include Google, Bing, YouTube, and TikTok. Threat actors abuse these well-known services because SEGs do not scan the URLs that the services redirect to, only the services that are typically known to be reputable. Some legitimate marketing tools, such as SendGrid, are also used to redirect to credential phishing content, but as they require more effort on the part of the threat actor, they are less frequently used.
QR Codes
An increasingly common method of bypassing SEGs is the use of QR codes. These QR codes can be either directly embedded in the email or in attached files such as PDFs or Microsoft Word documents. Cofense released an article highlighting some of the core characteristics of QR code phishing emails, as well as one highlighting what content can be embedded in attached Office documents.
Other Methods
Another method of bypassing SEGs that Cofense has written about is when threat actors use a SEG-encoded URL which is then scanned by the targeted victim’s SEG. This tactic works because many SEGs allow URLs that are already SEG-encoded because they appear to have already been analyzed.
Credential Phishing Kit Pages
Credential phishing pages are typically built by “kits” purchased by threat actors from other threat actors. This enables threat actors with relatively little skill to set up very convincing credential phishing pages for minimal cost and with minimal effort. These kits have varying levels of capabilities and quality, with the most expensive ones having multiple defensive methods, being indistinguishable from the legitimate login page, and being capable of bypassing multi-factor authentication. The more advanced kits used by threat actors have multiple defensive methods in place to prevent detection and investigation by security researchers and advanced security tools. The following sections detail some of the more common as well as the more troublesome tactics used by threat actors in these kits.
Geo Filtering
The most commonly seen feature used by threat actors as part of credential phishing kits is geolocation filtering. This is typically done via an IP lookup of the victim computer. Some kits use external sources that are queried directly by the credential phishing page, while others do the query on the back end, where victims and security researchers cannot see it. One of the most commonly used services for credential phishing kits is hxxps[://]get[.]geojs[.]io/v1/ip/geo[.]json. This service returns a large amount of information, but the information used by the kit typically includes the IP address, the country, the time zone, and the organization the IP is registered to. This information can typically be used to detect if a victim is using a VPN service as well as which one. If certain criteria are not met, then visitors are redirected to a legitimate page or simply met with a not found message.
Browser User-Agent and Language Filtering
Most credential phishing kits and many legitimate sites use a method of detecting the User-Agent of the browser visiting them, and some even detect the language. For legitimate sites, this information is used to determine what and how the page should render, as well as potential information about the user’s region. Credential phishing kits will often redirect browsers with User-Agents not matching a list to a legitimate site, such as Wikipedia. Some examples of User-Agents being filtered are:
- When a campaign uses a QR code, the User-Agent is typically examined to see if it is coming from a mobile browser. If the User-Agent is not, then the page will usually redirect to a legitimate page, like Microsoft.
- For some Mispadu campaigns, the sites hosting the malware download will not load if the language of the browser is not set correctly. For example, if the language is set to en-US rather than es-MX, then the browser will simply display a blank page.
- On pages that have ClickFix, they will frequently detect if the User-Agent is for something other than Windows and warn that the page only works on Windows machines.
CAPTCHA
CAPTCHA challenges are a well-known tool for preventing bots from accessing pages. They are used just as frequently by threat actors as they are by legitimate websites. Some CAPTCHAs have built-in detection of User-Agents, geo-ip, and other browser characteristics, which can be used to filter out traffic in addition to the simple interactive tests. This encourages threat actors to use free services such as Cloudflare Turnstile, which have these methods built into them, preventing security researchers from using Tor or some VPN services without the threat actor having to use any detection services of their own. Some websites purport to contain a CAPTCHA but instead contain ClickFix, which is used to deliver a malicious script when the CAPTCHA is “passed”. This is becoming increasingly common in malware delivery phishing campaigns.
Developer Tools Detection
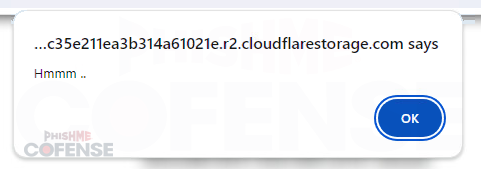
Figure 1: Message displayed by some credential phishing kits when developer tools are detected.
Security researchers often use developer tools built into various browsers, such as the inspect element ability or the logging of network traffic. This enables them to track website activity and monitor behavior such as HTTP POSTS of entered credentials to external sources. Threat actors have realized that security researchers make use of these tools, and many credential phishing kits now include detection methods that either redirect upon detection of developer tools or simply permanently suspend execution of the page.
Email Address Filtering
When a victim enters an email address into a credential phishing site, most modern phishing kits then compare the input email address, or at least the domain name of the email address, against a list provided by the threat actor. This has multiple purposes. Firstly, the domain name can be used to customize the login screen to make it seem more relevant to the victim. Secondly, the domain name can be compared to the list, and if it does not match, then the email likely belongs to a security researcher, so the page redirects to a legitimate site. If a threat actor wants to be even more precise, they can use a list of specific email accounts that were targeted by the credential phishing emails. Threat actors can further restrict access by sending a “verification” email with a link or code to the email address entered (if it matches the approved list), as seen in Figure 2. As security researchers do not typically have access to the inboxes of victims, this can effectively stymie analysis.
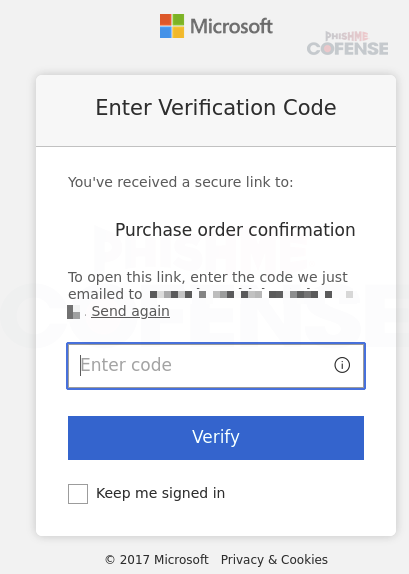
Figure 2: Verification prompt after matching credentials are entered.
Password Protection
Threat actors can use password protection at several different steps in the process. Depending on the step, the password protection can help prevent detection by SEGs, browsers, or even EDRs.
- The most commonly used option is to password-protect downloaded archives, which prevents SEGs and browsers from scanning the contents.
- Some threat actors may also password-protect attachments, such as those using attached PDFs to deliver malware like Mispadu.
- Finally, threat actors may password-protect the actual credential phishing pages themselves or pages that link to them, as seen in Figure 3.
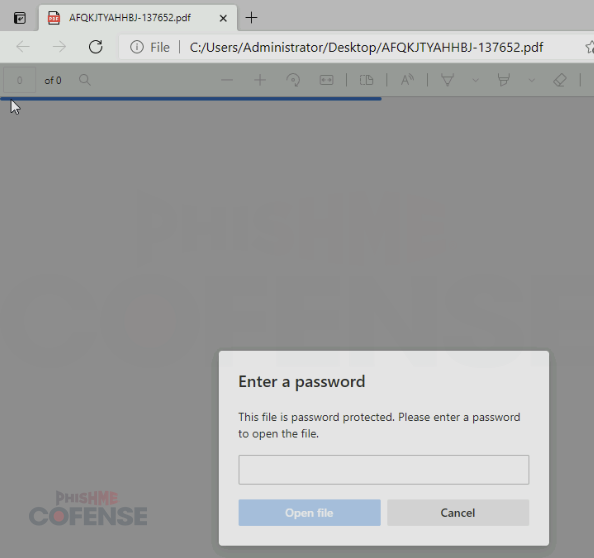
Figure 3: Password protected attached PDF delivering Mispadu.
Quick Deploy Hosting
One of the more common ways that threat actors avoid having their infrastructure taken down is to use quick deploy hosting that can upload static websites via a command-line utility. With this type of hosting, threat actors use single-use subdomains that are only used for one campaign, cost little to nothing, and are easy to deploy with a simple command rather than needing a multi-step process to design and deploy. Another benefit to threat actors of quick deploy hosting is that it uses subdomains. Many automated defenses use domain aging to calculate if something is suspicious, but domain aging does not work for subdomains. Some quick deploy hosting domains that are known to have a mix of legitimate and malicious subdomains include:
Table 1: Examples of Quick Deploy Hosting services.
Domain | Example Malicious Subdomain |
.workers[.]dev | c1ient-indrctd1oadinn[.]distribute-employees-bonuses[.]workers[.]dev |
.glitch[.]me | chalk-azure-primula[.]glitch[.]me |
.pages[.]dev | sun-shine[.]pages[.]dev |
.blob[.]core[.]windows[.]net | projectdesignarchitectsd[.]blob[.]core[.]windows[.]net |
.netlify[.]app | 67d430dcca6bc236023002a9[.]netlify[.]app |
.r2[.]dev | pub-c76b55d7b18c4d2c9888b98bb5e977d1[.]r2[.]dev |
.trycloudflare[.]com | hardcover-recognized-real-collective[.]trycloudflare[.]com |
Conclusion
Threat actors use a wide variety of TTPs to prevent detection of their tools and services both via phishing pages and the emails used to deliver their phishing campaigns. The TTPs involved affect both human analysts and automated solutions (which are often driven by AI). As threat actors adapt to the methods used to analyze their campaigns, so too must defenders adapt their approaches and improve their tools to bypass the new defenses. Some TTPs such as CAPTCHA gated pages are already being automatically solved by developing AI technologies. Others, such as geo filtering and browser User-Agent filtering, can be manually bypassed with effort by human analysts who are gradually automating the process. AI-based tools may seem the best way to bypass most of the threat actor’s preventive measures, but it is important to note that threat actor’s offensive AI often develops faster than legitimate defensive AI and will likely come up with new defenses at the same rate as the old defenses are solved. It is important for analysts and decision makers to understand the current TTPs threat actors use as well as the TTPs that are likely going to see increased usage, such as email address filtering and quick deploy hosting.
Mitigation
Many of the methods used by threat actors to evade detection can easily be bypassed by security researchers and Security Operations Center (SOC) teams willing to put forth some effort. This is because threat actors are more likely to face detection by automated systems than by analysts, so they have prepared accordingly. Some of the tools that an analyst can use are to manually select a User-Agent to spoof, pick a VPN endpoint country that bypasses credential phishing kit geo filtering, and enter passwords stored in one location into a different location. Automated systems should be tuned to be suspicious of subdomains residing on popular quick deploy hosting services. AI-driven and automated defenses, as a whole, are decently effective at filtering out malicious emails, however, where they truly fall behind is in the steps after an employee has clicked a link in an email. It is vital that AI-driven and automated defenses be augmented by trained employees. To learn more about the case for controlled AI automation through human supervision, sign up for our 3-part webinar series exploring the challenges of relying solely on AI-driven solutions for phishing defense.