The first steps in traditional phishing emails have remained the same for decades; the email will contain either a malicious URL or an attachment. In recent years, however, URLs embedded in phishing emails as an initial means of engaging the intended victim have reached those intended victims at a much higher rate than attachments used for the same purpose. Our data from the past year shows that the dominance of URLs over attachments continued in 2022 for several reasons, including abusable trusted domains, free services on the web that provide phishing infrastructure, and the evasive effects of redirects.
High Percentage of URL-based Phishing Associated with CredPhish
This continuing trend of URL-based dominance occurs among phishing emails reaching enterprise-level organizations, many of which are protected by high-profile secure email gateways (SEGs).
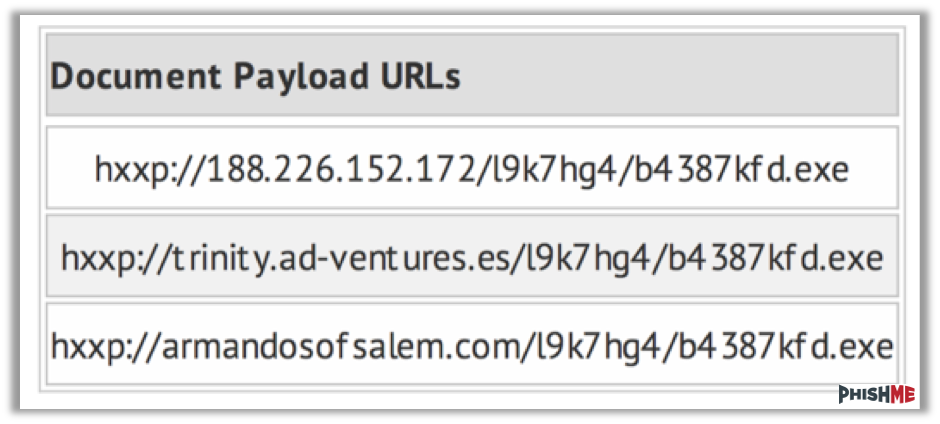
Figure 1: Share of URL-based vs. attachment-based phishing emails reaching inboxes in 2021 and 2022
There are a number of possible reasons that URL-based phishing emails may escape SEG detection more easily than attachment-based emails. URLs may have an inherent level of trust if trusted domains are abused; SEGs may be better at identifying malicious files than URLs; a large percentage of benign marketing emails contain URLs from unknown sources and are thus difficult to differentiate from malicious URLs from unknown sources. Beyond the SEG, threat actors have even more reason to use URLs, as users in today’s work environment may be more comfortable interacting with an unknown link than an unknown attachment. The two charts in Figure 1 show that the share of URL-based phishing emails did not change significantly between 2021 and 2022 but continues to outpace the effective use of attachments by a factor of four. The use of attachments increased its share of the total by approximately three percent.
Traditional phishing emails generally have the objective of stealing credentials or delivering malware. Attached files and embedded URLs can both be used for either one of these objectives. Figure 2 shows that despite malware delivery emails making higher use of attachments as an engagement method than credential phishing emails do, both are primarily initiated by an embedded URL.
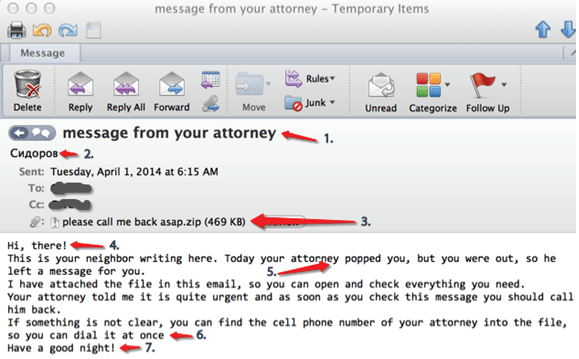
Figure 2: 2022 Comparison of malicious links and attachments used for credential phishing and malware delivery.
Generally, we expect to see a higher percentage of URLs with credential phishing. This is mostly attributable to the fact that most variants of credential phishing already require the use of URLs. Phishing-as-a-Service and other marketed prebuilt phish kits often favor the use of URLs. The use of attachments is still common enough, however, and file types such as HTML and PDF are among the most common in credential phishing email attachments.
As noted, the use of attachments in malware delivery is more prominent than what we see in credential phishing campaigns. This is likely because most malware delivery already requires the use of files as the final payload, meaning that the threat actor is already somewhat familiar with the use of files. It is also very common for threat actors attempting to deliver malware to include their malicious files in password-protected ZIP archives which can disrupt SEG analysis. This adds to the number of phishing emails we see reaching end users. Additionally, some of the more advanced malware families that are disseminated at a high volume, like QakBot and Emotet, are known to use attachments in their emails, but they do employ the use of embedded URLs as well.
Phishing URLs and their Evasive Tactics
Phishing URLs are currently the most popular engagement method used within phishing emails reaching inboxes. The phishing tactics threat actors employ that are known for bypassing email security infrastructure contribute to this. Phishing URLs reaching end users frequently use one of the following tactics in embedded URLs (although other tactics also exist):
- Trusted Domains – Trusted services, such as cloud services, are often abused by threat actors to host malicious content. This means their phishing sites will be on domains that are viewed as trusted by end users and security infrastructure like SEGs. Phishing emails abusing these services are often successful at reaching intended targets since these domains cannot be outright blocked.
- Openly Available Services – Threat actors often seek free or cheap services to abuse within their phishing campaigns. Often times this can even result in their URLs having a trusted domain as well. Any free or cheap hosting platform is at risk of being abused by threat actors seeking a cheap way to
- Multiple Redirects – It is a common tactic that the URL embedded in the phishing email is not the first stage of the phishing attack. By using multiple redirects and creating a chain of malicious URLs to be analyzed, threat actors can often have enough redirections from the initial URL to the final page that is directly used to download malware or steal credentials that a SEG may stop analysis before reaching it.
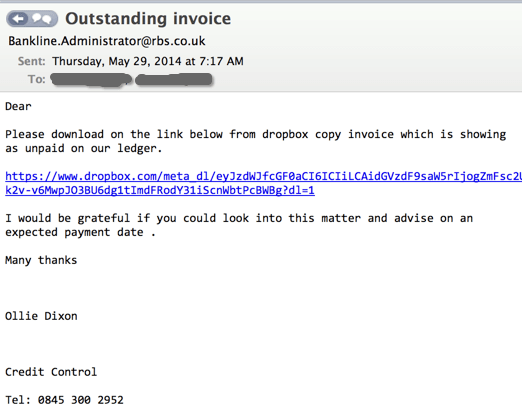
Figure 3: Example of a phishing email using a malicious link.
Malicious Attachments Configured to Reach Inboxes
There are many potential tactics that can be employed in order to effectively use malicious attachments within phishing emails. Malicious attachments have a great variety of uses, including directly harvesting credentials, containing other malicious files that have been compressed, redirecting to a phishing URL, and acting as a first stage downloader for malware, among many other possibilities. Further, the type of attachment used often depends on the threat being delivered. Some of the most common tactics we see used in phishing emails that contain a malicious attachment are:
- Password Protected Files – It is common for threat actors to use password-protected files such as a ZIP archive to bypass security and reach intended targets. Emotet is notorious for using this tactic and often disseminates a large number of emails with malicious Office files compressed into password-protected ZIP archives. The password is often in easy-to-access areas for the intended target to find, such as the email body.
- Unfamiliar Attachments – Threat actors frequently seek out new types of attachments that may be unknown to security researchers and have a chance of bypassing SEGs. Most SEGs will easily capture and block a directly attached malicious executable file due to the simplistic and obvious nature of the threat. However, threat actors are aware of this and recently we have seen QakBot operators send out directly attached .ONE files which seem to effectively evade SEG scrutiny.
- Encoded Files – File encoding is a popular way of making malicious attachments difficult to analyze. HTML files are a very popular file type for threat actors to encode, but encoding is a common tactic seen across a variety of file types.
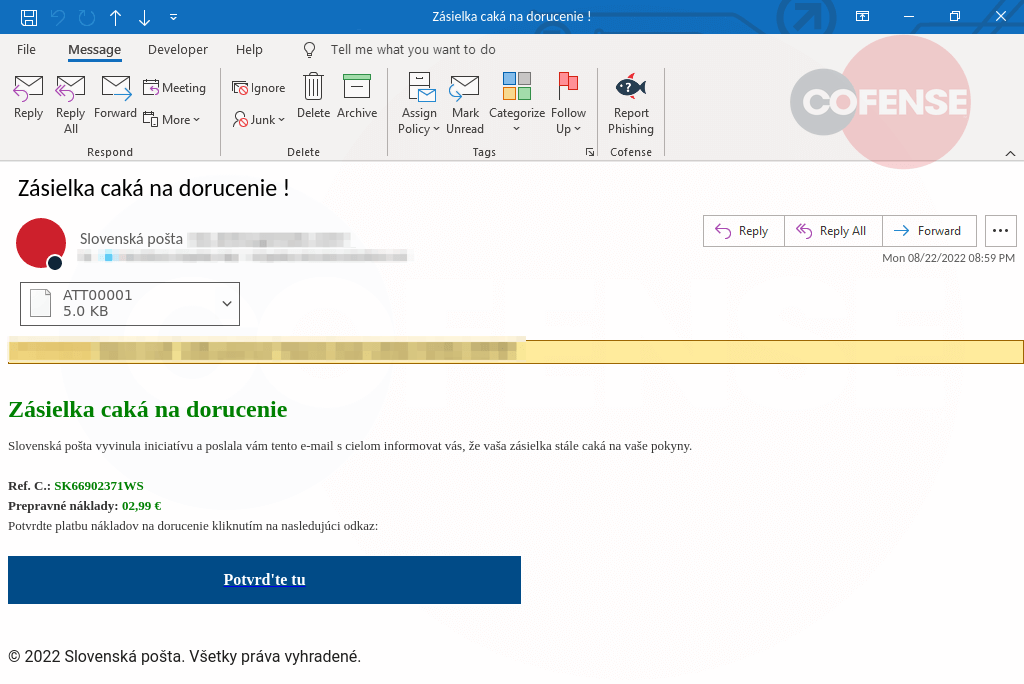
Figure 4: Example of a phishing email using a malicious attachment.