Microsoft 365 EOP
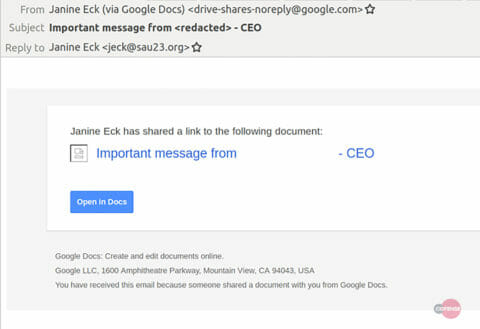
Cofense IntelligenceTM has identified a highly customized credential phishing campaign using Google Drive to target a company within the energy sector. This phishing campaign is crafted to look like the CEO of the targeted company has shared an important message with the recipient via Google Drive. The email is legitimately sent by Google Drive to employees and appears to be shared on behalf of the CEO by an email address that does not fit the email naming convention of the targeted company. By using an authentic service, this phishing campaign was able to bypass the email security stack, in particular Microsoft Exchange Online Protection, and make its way to the end user.
The technique of using Google Drive to disseminate a phishing email helps bypass email security measures because of the difficulty of blocking a legitimate business service. The link within the email body is also hard to defend against because it links to an actual Google Drive share. If the organization’s email body inspection tool does not examine past the first link, phishing countermeasures will mark the email as non-malicious, allowing the phish to avoid another security measure. Even if the security appliance were able to look past the initial link, the secondary links would not be shown in Google Drive as documents unless they are downloaded or viewed through the file browser. Once the user has accessed the document on Google Drive, they are presented with an explanation of a public business decision and asked to view the related document via another link.
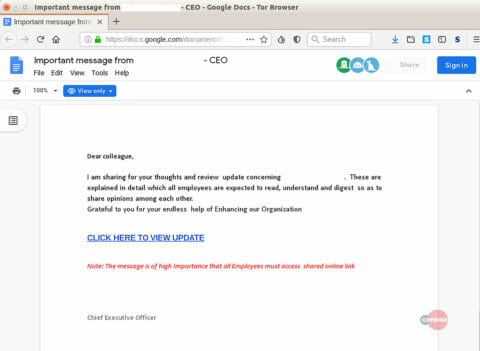
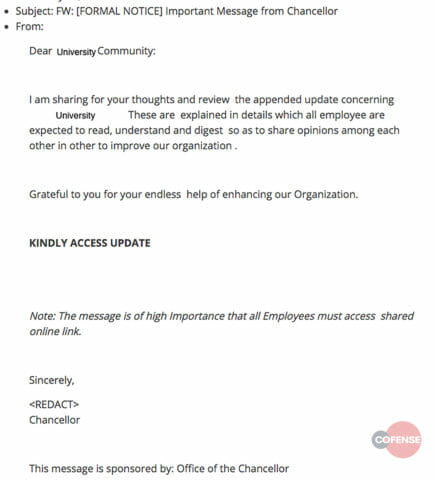
The document used in this campaign was highly tailored to the targeted energy sector company. The key information used in their social engineering template included the CEO’s name, the business decision, and the company logo. However, this information was outdated by a year and is no longer accurate or pertinent to the recipient. Sections of this document also suggest that it is part of a template used to craft customized phishing campaigns. Two sentences found in the Google Drive document, ‘Grateful to you for your endless help of Enhancing our Organization’ and ‘Note: The message is of high Importance that all Employees must access shared online link’, have been spotted in a similar phishing campaign targeting secondary education facilities.
If the end user opens the link inside the Google Drive document, they will be redirected to a fake login page created on August 1st. If the victim enters their credentials, the credentials will be exfiltrated back to the threat actor for use at a later time. One automated security mechanism that might be able to defend against this part of the attack scenario is a network content filtering appliance keyed on blocking newly registered domains. This security mechanism would have stopped the end user from getting to the fake login page because of the registration date of the website.
Even if a network security appliance with the capabilities to stop the user from getting to the login page was used, the phishing email still got through. The legitimacy of Google Drive allows for these phishing campaigns to bypass an organization’s email security stack, namely due to the shortcomings of the email content filtering’s link analysis component. Using technology to secure users from these types of campaigns is only half the solution — it is vital to implement security awareness programs that educate users about these threats and enable them to report suspicious emails suspicious emails. Cofense ReporterTM and Cofense PhishMeTM enable associates by providing an easy phishing report button and employee education for resiliency against phishing.
Phishing email that directs end users to the Google Drive document
Document hosted on Google Drive that targeted an energy sector company
Same phishing email used to target a university
Appendix
Yara Rule: PM_Intel_CredPhish_27117
ATR ID: 27117
| IOC |
| hxxps://reventity[.]com/citrixshare/scan[.]html |
HOW COFENSETM CAN HELP
75% of threats reported to the Cofense Phishing Defense CenterTM are credential phish. Protect the keys to your kingdom—condition end users to be resilient to credential harvesting attacks with Cofense PhishMe.
Over 91% of credential harvesting attacks bypassed secure email gateways. Remove the blind spot—get visibility of attacks with Cofense Reporter.
Quickly turn user-reported emails into actionable intelligence with Cofense TriageTM. Reduce exposure time by rapidly quarantining threats with Cofense VisionTM.
Attackers do their research. Every SaaS platform you use is an opportunity for attackers to exploit it. Understand what SaaS applications are configured for your domains—do YOUR research with Cofense CloudSeekerTM.
Thanks to our unique perspective, no one knows more about the REAL phishing threats than Cofense. To understand them better, read the 2019 Phishing Threat & Malware Review.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks.