By Alan Rainer and Max Gannon
The infamous malware family Emotet—also known as Geodo—has fully resurfaced and resumed sending phishing campaigns that trick users into clicking on links and downloading attachments that contain malicious macros. Many of the emails feature common financial themes that capitalize on an existing reply chain or contact list impersonation.
In most cases, subjects for these phishing emails are rather mundane, such as “RE: Re: Contract/Invoice Count” and “Customer Statement 09/16/2019”, with attachments that use Microsoft Office macros to install malware. Upon installation of the Emotet executable, the banking Trojan TrickBot may be placed onto the victim machine, mainly depending on geography and organization. TrickBot is known to siphon information from a host and has shown to result in Ryuk ransomware making its way to the victim after some time. Current statistics show that Emotet is targeting over 66,000 unique emails on more than 30,000 domains. The origin emails—of which credentials had likely been stolen—span over 1,900 unique domains from 3,400 different senders. This extensive reach makes it tricky to combat the Emotet threat.
User awareness and technical safeguards such as email defense capabilities and endpoint protection solutions are vital in thwarting Emotet. Users should be increasingly wary of reply chain emails that contain unexpected documents, especially ones that ask to ‘Enable Content’ for editing or to ‘Accept the license agreement.’
Security teams should maintain a heightened awareness of Emotet trends and leverage the analysis to deny or hunt down malicious activity. Through active monitoring of the Emotet botnet and malware, Cofense IntelligenceTM continues to identify phishing threats that may impact customers and to provide security operations with the latest campaign data. In the Technical Findings section below, Cofense Intelligence has chosen a random example of the most common email and macro as seen today for analysis.
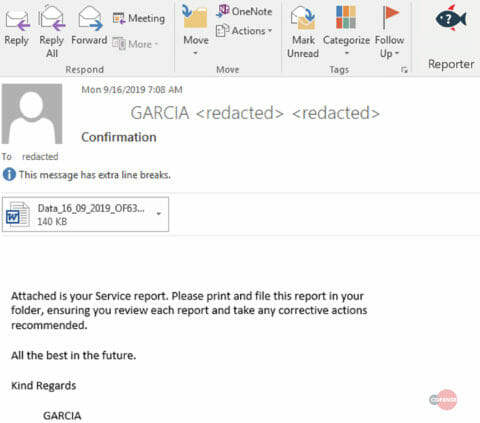
Figure 1: Original Email
Technical Findings
Emotet delivers malicious documents as either part of a reply chain or as a finance-themed (such as invoice, new document, bank transfer, and quotation) phishing email. The languages used for each email body differ widely and have been seen to include English, Italian, Polish, or German, among others. These phishing emails contain a Microsoft Word document with a .doc extension and an Office macro that downloads Emotet executables.
Historically, Emotet utilized malicious links as well, but current indications show this is not the preferred method of malware delivery. The attached Office documents with macros store payload information in embedded object data, rather than in the macro itself, which makes analysis more difficult.
While similar to a delivery mechanism discussed in a previous blog, this version of the dropper is more advanced than before. When the document is opened, it displays a lure stating that to continue to use Microsoft Word after September 20, 2019, the user must accept the license agreement and enable editing. The lure shown in Figure 2 does not appear to be significantly different from the typical Office message that asks to enable macros; however, a requirement to accept a new license agreement makes the lure seem so routine that this new trap may be more effective.
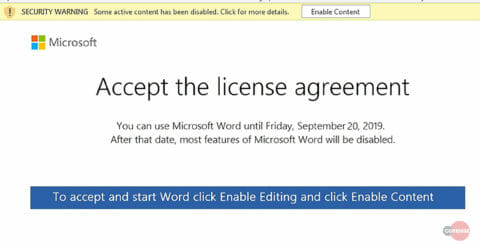
Figure 2: Macro Request
After Office macros are enabled, Emotet executables are downloaded from one of five different payload locations. When run, these executables launch a service, shown in Figure 3, that looks for other computers on the network. Emotet then downloads an updated binary and proceeds to fetch TrickBot if (currently undetermined) criteria of geographical location and organization are met.
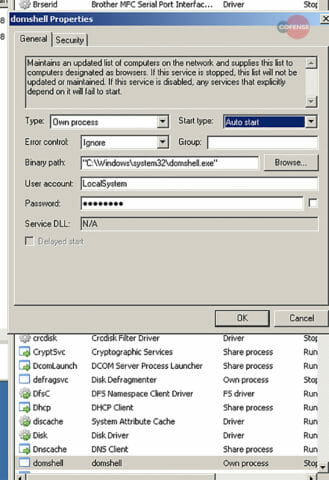
Figure 3: Service Launched by Emotet
The macros used in this case are relatively small even with the garbage code included, totaling approximately 150 to 300 lines. Removing the garbage code reveals only 10 lines of actual code. This code extracts metadata from embedded objects in the Word document; specifically, the “caption” data of these objects as seen in Figure 4.
![]()
Figure 4: Object content
While the attached documents all have a .doc extension, they are in fact .dotm, .docx, and other document file types, which enables them to successfully hide the embedded objects as ActiveX objects rather than typical “Form” objects whose metadata can be easily accessed in an opened document.
In each case, the result is the attempted download of an Emotet binary from a set of five payload locations using both HTTP and HTTPS. Emotet has been seen downloading TrickBot and other malware historically, with no noteworthy modifications to the present-day TrickBot sample.
How Cofense Can Help
Cofense Resources
Cofense PhishMeTM offers a phishing simulation, “Service Report – Emotet,” to educate users on the phishing attack described in today’s blog.
89% of phishing threats delivering malware payloads analyzed by the Cofense Phishing Defense CenterTM bypassed email gateways. Condition users to be resilient to evolving phishing attacks with Cofense PhishMeTM and remove the blind spot with Cofense ReporterTM.
Quickly turn user reported emails into actionable intelligence with Cofense TriageTM. Reduce exposure time by rapidly quarantining threats with Cofense VisionTM.
Easily consume phishing-specific threat intelligence to proactively defend your organization against evolving threats with Cofense Intelligence.
Thanks to our unique perspective, no one knows more about REAL phishing threats than Cofense. To understand them better, read the 2019 Phishing Threat & Malware Review.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats.


