By: Kian Mahdavi & Adam Martin, Cofense Phishing Defense Center
The Cofense Phishing Defense Center (PDC) has recently derived a stealthy malware campaign that we believe shares an abundance of attributes with the malware-as-a-service Buer Loader. The authors have taken the rare stride of rewriting their malicious downloader in the unfamiliar Rust programming language. We can only assume this decision was executed in a bid to slow down forensic research analysis, avoid detection and, most importantly, slip past as many secure email gateways (SEGs) as possible.
The threat actors behind the attack have really upped their game by incorporating high-quality Covid-19 communication themed references. They inform the reader there is “urgent information on the latest research from Centers for Disease Control and Prevention (CDC) and Food and Drug Administration (FDA) in the field of vaccines against the COVID-19.” There’s already an abundance of global discussion regarding the health and safety of the program and, as a result, this naturally reels in inquisitive readers.
Let’s explore more:
Figure 1: Email Body
Delivery
The subject line reads: “Covid-19 Vaccination Information.” Logically, this would be the first chunk of data the reader would come across in their inbox – an email that users would likely be expecting, given recent vaccination rollouts globally. Nothing unusual here?
The email derives from a cleverly crafted but newly created domain name that’s only a few weeks old (as of this writing). The top-level domain (TLD) contains the all-important Covid-19 reference, as well as an abbreviation of “information” – at least that’s what we assumed:
@cov19inf[.]com
Furthermore, the opening of the email doesn’t contain phrases such as, “Good Morning” or “Dear…”, possibly indicating this is a mass-email attack sent to many individuals. The threat actors understand the power of social engineering, and how to not only outwit users but also frighten and manipulate. Mentioning severe life-long complications, post-vaccine, is enough to send cold shivers down anyone’s spine. Worse still, federal agencies such as CDC and FDA have been included within the email body. We noted that multiple Covid-19 vaccines were stated, further widening their scope and encouraging users to engage.
Lastly, there’s this: “You were assigned personal access to the attached, your passcode: ***”. This is the secret recipe required to ignite the malicious downloader into the victim’s computer. With the personal touch added, users could be motivated to take it more seriously, had they not done so a moment ago.
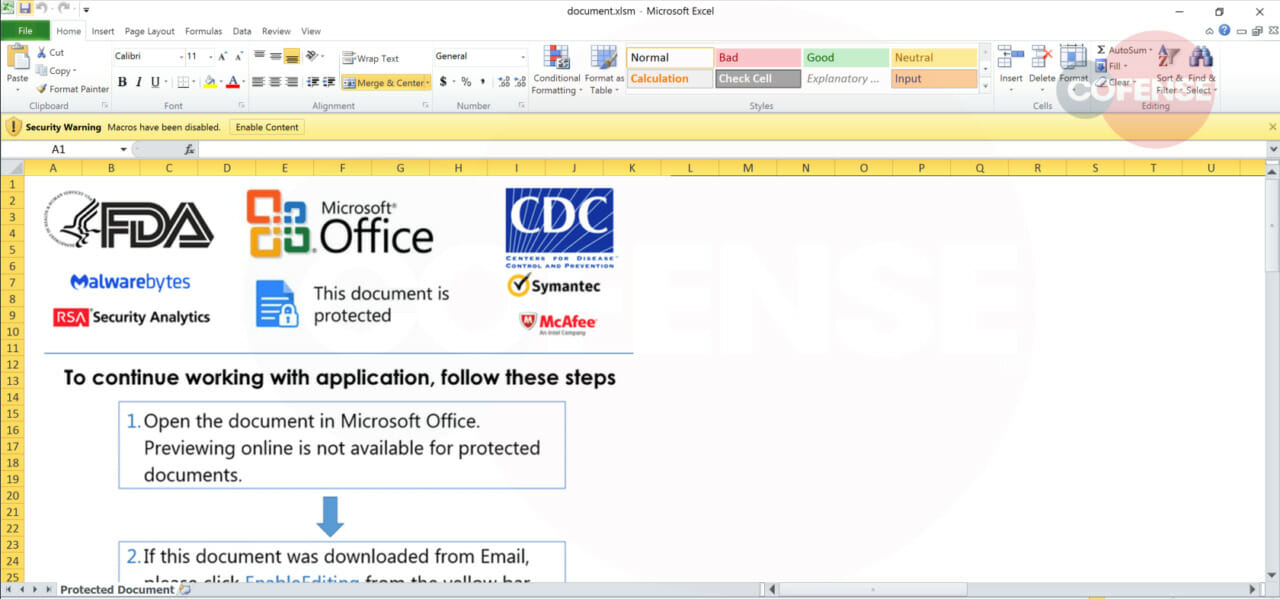
Figure 2: Password Protected – Document.xlsm – Generic Naming
Infection Chain
The threat actor baits the victim into clicking the “Enable Editing” button to initiate the embedded macro within the Microsoft Excel document. The macro then drops and runs a dynamic link library (DLL) within the ProgramData folder. Once the malicious DLL is executed, it then downloads a .XLS file that’s actually an executable, renamed and placed within the C:ProgramData. The file name is a randomly generated string and will be different for each infection as evident in Figure 6 below.
Initial Stage Malicious Files
File Name: document.xlsm
MD5: 0884e793587dc061b8ae69fc086ece83
SHA256: bd477b8eabe8baa2042f42b04d6afed2390afc1f3b5f7270538130f96b27e039
Size: 91136 bytes (89K)
File Name: test.dll
MD5: 2539dbed170613f776445dab9b62fac0
SHA256: dc8c2d326143ff4334a7bdbafcb821ee9a525eb3248e676e4940baab8d0626a9
Size: 6144 bytes (6.00K)
Second Stage Malicious Files
File Name: SignerLib.xls
MD5: 796b3e4674b68b33c906ce32c3275d83
SHA256: afb5cbe324865253c7a9dcadbe66c66746ea360f0cd184a2f4e1bbf104533ccd
File Size: 7115776 bytes (6M)
Second Stage Payload
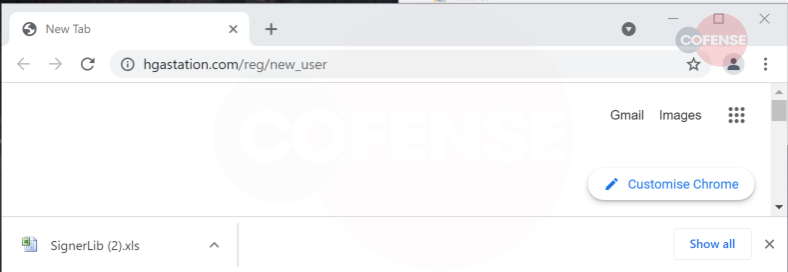
Payload URL Location: hXXps://hgastation[.]com/reg/new_user
IP Address:172[.]104[.]240[.]67
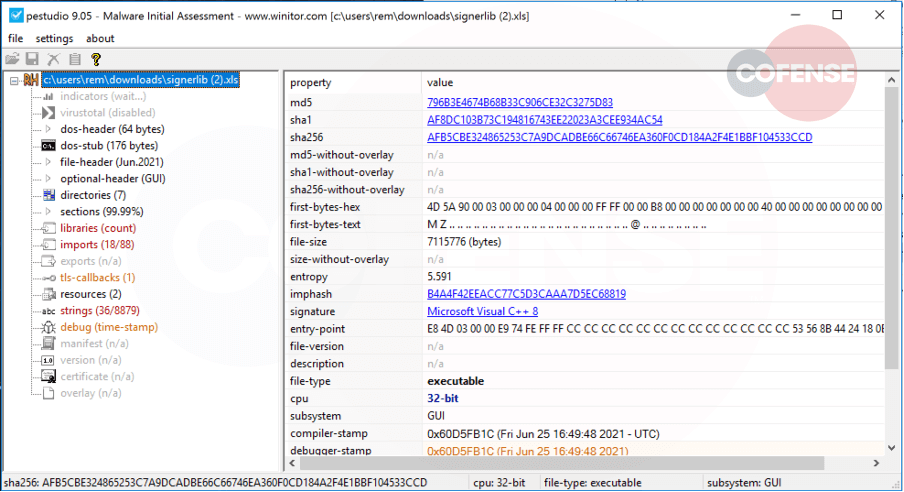
Once inspected in PE Studio, the .XLS file is in fact a PE Executable, as can be seen above the first HEX bytes, with 4D 5A confirming it as a PE file. It also contains an import table that will utilize several anti-analysis functions.
Second Stage Payload Icon
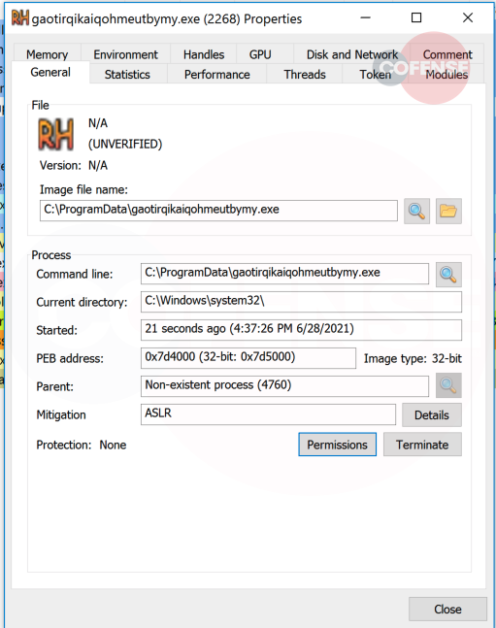
The malicious payload contained API calls, which are intentional and meant to help evade sandbox checks and detection from security vendors. This file contained several MITRE tactics such as IsDebuggerPresent and GetTickCount to evade detection, as illustrated below:
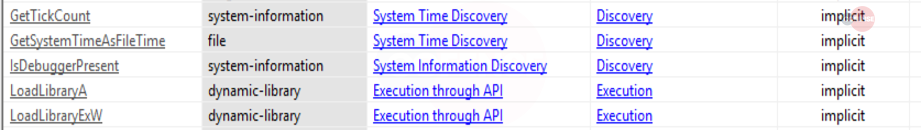
*Source: https://www.joesandbox.com/analysis/441008/0/html
This new variant of Buer Loader keeps the same C2 communication structure as the older strains. The initial C2 communication seems to be multi-layer encrypted and contains information about the compromised host. Based on past analysis, Buer Loader can be used to deliver other payloads including ransomware.
Command & Control URL: hXXps://usergtarca[.]com
IP Address: 76[.]58[.]124[.]186
Notable Discoveries
Should the malicious downloader successfully execute, the threat actors would be capable of the following, and more, notable threats:
- Granting threat actors access permissions to the targeted victim’s computer
- Creating backdoor access
- Altering administrative controls
- Modifying system files
- Distributing other malware, including ransomware
How Cofense can help
As mentioned in previous blogs, attackers regularly spread malware and invoice-themed credential phishing emails via attachments, now more than ever. Why? Because SEGs have a tough time auto-scanning wrapped URLs and screening for compressed attachments, making it almost impossible to examine the internal contents.
The Cofense PhishMe platform offers various simulation templates to assist and train users on all possible phishing tactics and evolving techniques described in this blog.
Thanks to phishing training, users have the necessary knowledge and know-how to look out for future phishing attacks and, if in doubt, the Cofense Reporter forwards threats to the Cofense PDC for analysis. Cofense Triage reduces real-time exposure and combines with Cofense Vision to quarantine such threats.
Lastly, Cofense Intelligence will precisely protect your organization against evolving threats. Cofense Intelligence customers received additional information about this threat in Active Threat Report (ATR) 198894.
Indicators of compromise
| File Name | document.xlsm |
| MD5 | 0884e793587dc061b8ae69fc086ece83 |
| SHA256 | bd477b8eabe8baa2042f42b04d6afed2390afc1f3b5f7270538130f96b27e039 |
| Size | 91136 bytes (89K) |
| File Name | SignerLib.xls |
| MD5 | 796b3e4674b68b33c906ce32c3275d83 |
| SHA256 | afb5cbe324865253c7a9dcadbe66c66746ea360f0cd184a2f4e1bbf104533ccd |
| Size | 7115776 bytes (6M) |
| File Name | test.dll |
| MD5 | 2539dbed170613f776445dab9b62fac0 |
| SHA256 | dc8c2d326143ff4334a7bdbafcb821ee9a525eb3248e676e4940baab8d0626a9File |
| Size | 6144 bytes (6.00K) |
| Payload Location | hXXps://hgastation[.]com/reg/new_user |
| IP Address | 172[.]104[.]240[.]67 |
| Command & Control URL | hXXps://usergtarca[.]com |
| IP Address | 76[.]58[.]124[.]186 |


